Advent of CTF – Day 3 Writeup
This writeup describes all steps necessary to solve Day 3 of the Advent of CTF challenges. The previous challenge can be found here: Advent of CTF – Day 2.
Just like day 1 and 2 this is yet another challenge that is preparing us for the real hard work later on!
Opening the challenge URL gives us the following page
Just like the previous two challenges let’s open up the page source and check for any “out of the order” or obvious things.
On the bottom of the HTML stack, just above the closing </body> tag we see a JavaScript file called login.js. Let’s check out the content of this file!
function checkPass()
{
var username = document.getElementById('username').value;
var password = document.getElementById('password').value;
var novi = '-NOVI';
if (password == btoa(username + novi)) {
window.setTimeout(function() {
window.location.assign('inde' + 'x.php?username='+ username +'&password=' + password);
}, 500);
}
}
After a bit of inspection we can deduct that this code checks whether our password has the same value as our username + -NOVI encoded to Base64. Let’s try to do just that then!
For our username we can use OBZ which means our final username inside of the code becomes OBZ-NOVI. Next, we encode this to Base64 which results in
T0JaLU5PVkk=
Our final login screen looks like this
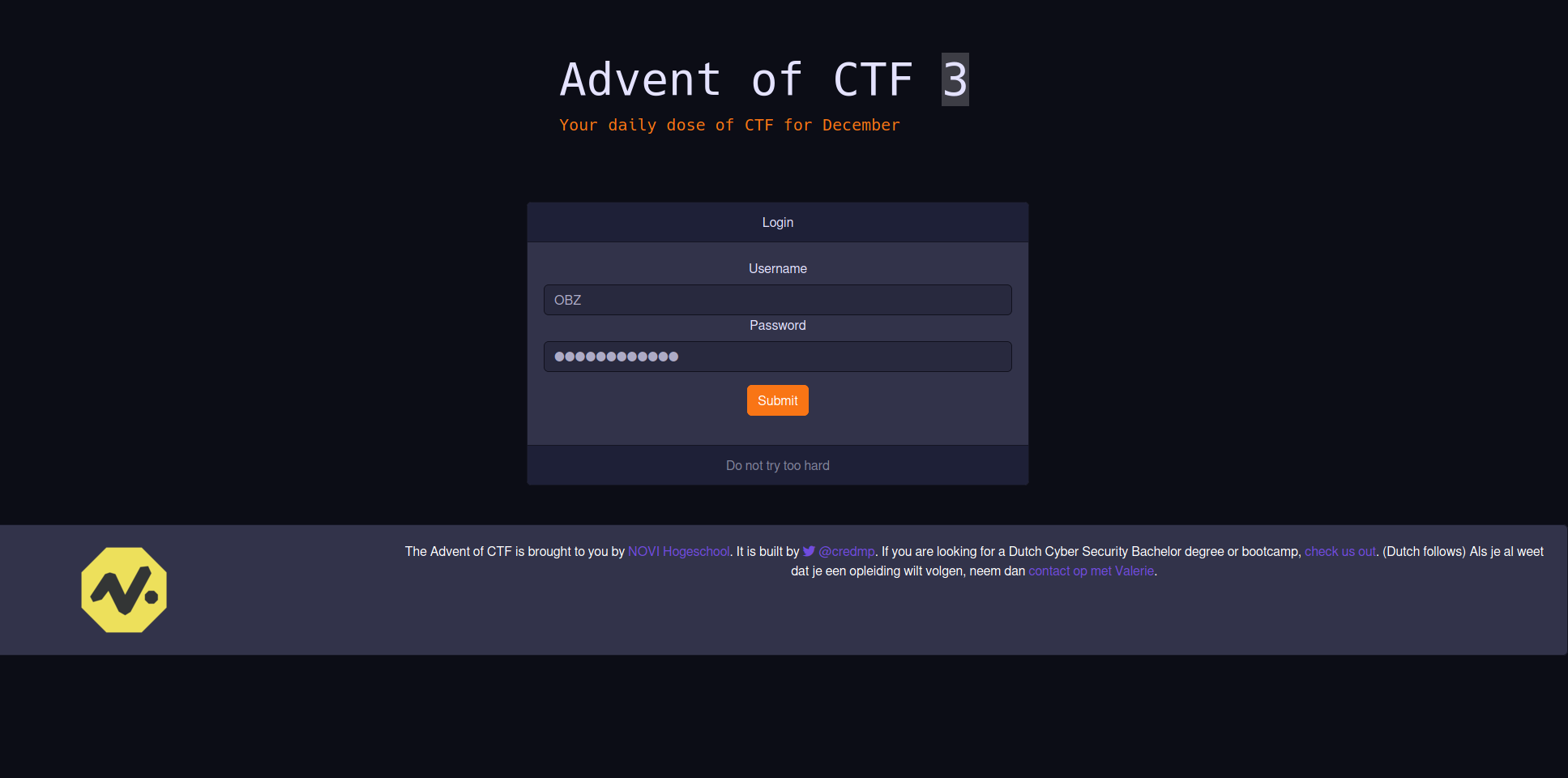
Hitting submit gives us the flag for this challenge! The flag is: NOVI{javascript_is_not_s@fe}
On to the next challenge: Advent of CTF – Day 4 Writeup









2 Comments