Advent of CTF – Day 4 Writeup
This writeup helps you solve the Day 4 challenge of the Advent of CTF challenges. The previous challenge can be found here: Advent of CTF – Day 3 Writeup.
Today’s challenge is a bit more on the tricky side and requires us to do a couple things so let’s get right into it!
Opening the challenge URL gives us the following page
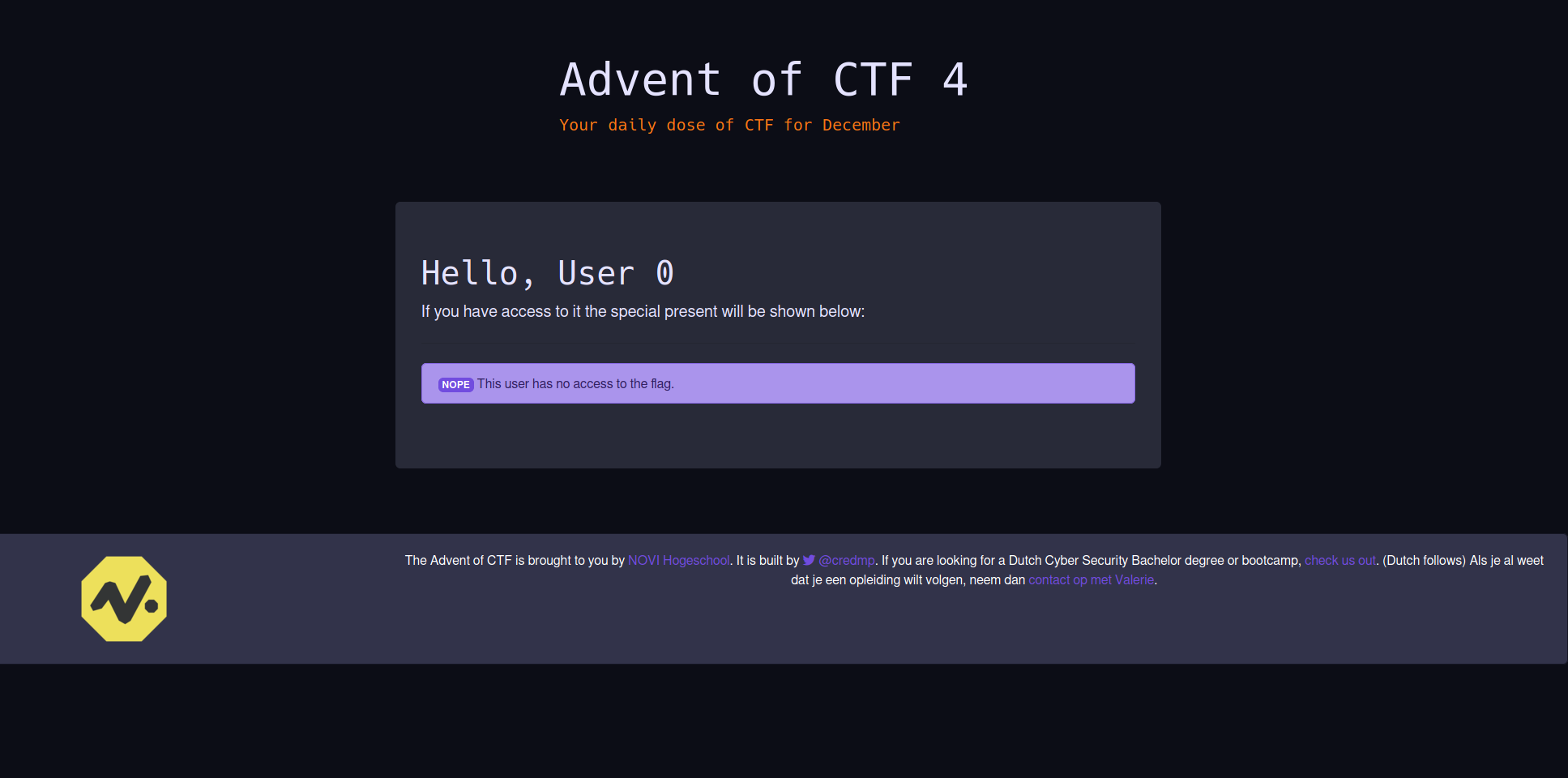
On first sight we can see that we are User 0 so somewhere it should’ve registered us as this specific user. We can find a JavaScript file called login.js when scrolling through the page source. Inside this file is the following content:
function startup() {
key = localStorage.getItem('key');
if (key === null) {
localStorage.setItem('key', 'eyJ1c2VyaWQiOjB9.1074');
}
}
var _0x1fde=['charCodeAt'];
(function(_0x93ff3a,_0x1fded8){
var _0x39b47b=function(_0x54f1d3){
while(--_0x54f1d3){
_0x93ff3a['push'](_0x93ff3a['shift']());
}};
_0x39b47b(++_0x1fded8);
}(_0x1fde,0x192));
var _0x39b4=function(_0x93ff3a,_0x1fded8){
_0x93ff3a=_0x93ff3a-0x0;
var _0x39b47b=_0x1fde[_0x93ff3a];
return _0x39b47b;
};
function calculate(_0x54f1d3){
var _0x58628b=_0x39b4,_0xc289d4=0x0;
for(let _0x19ddf3 in text){
_0xc289d4+=text[_0x58628b('0x0')](_0x19ddf3);
}return _0xc289d4;
}
function check() {
key = localStorage.getItem('key');
hash = window.location.search.split('?')[1];
if (key !== null && hash != 'token='+key) {
parts = key.split('.');
text = atob(parts[0]);
checksum = parseInt(parts[1]);
count = calculate(text);
if (count == checksum) {
setTimeout(function(){
window.location="index.php?token=" + key;
}, 5000);
}
}
}
startup();
check();
A couple things are obfuscated but we might not need to know what they do altogether. The important thing here are the startup() and check() methods
The startup() method sets a localStorage key called key for us and sets the value to eyJ1c2VyaWQiOjB9.1074.
The check() method does some extracting and calculations. In order for us to exploit this credential check we will need to adjust the two parts of the key: eyJ1c2VyaWQiOjB9 and 1074.
First, let’s start with the Base64 encoded string eyJ1c2VyaWQiOjB9. Decoding this gives us {"userid":0}. Let’s change the 0 to a 1 and encode it again so we get eyJ1c2VyaWQiOjF9.
Next, we will use the calculate method to calculate the number we need to append after our newly made Base64 string. From the code we can deduct that calculate requires a text variable. So through our browser inspector we can execute the following
const text = '{"userid":1}';
calculate(); // 1075
Now we need to combine our Base64 string and our just calculated number. Our final string looks like this:
eyJ1c2VyaWQiOjF9.1075
If we paste this as our localStorage value for key key and remove the ?token=eyJ1c2VyaWQiOjB9.1074 from the URL in the address bar, we should see our flag afer we refresh the page in a couple seconds! The flag is: NOVI{0bfusc@t3_all_U_w@n7}
On to the next challenge: Advent of CTF – Day 5 Writeup








2 Comments