Advent of CTF – Day 5 Writeup
This writeup helps you solve Day 5 of the Advent of CTF challenge. The writeup for the previous challenge can be found here: Advent of CTF – Day 4 Writeup.
Today’s challenge requires us to use a class “hacking tool” in order to complete it. Let’s check it out!
Opening the challenge URL gives us the following page
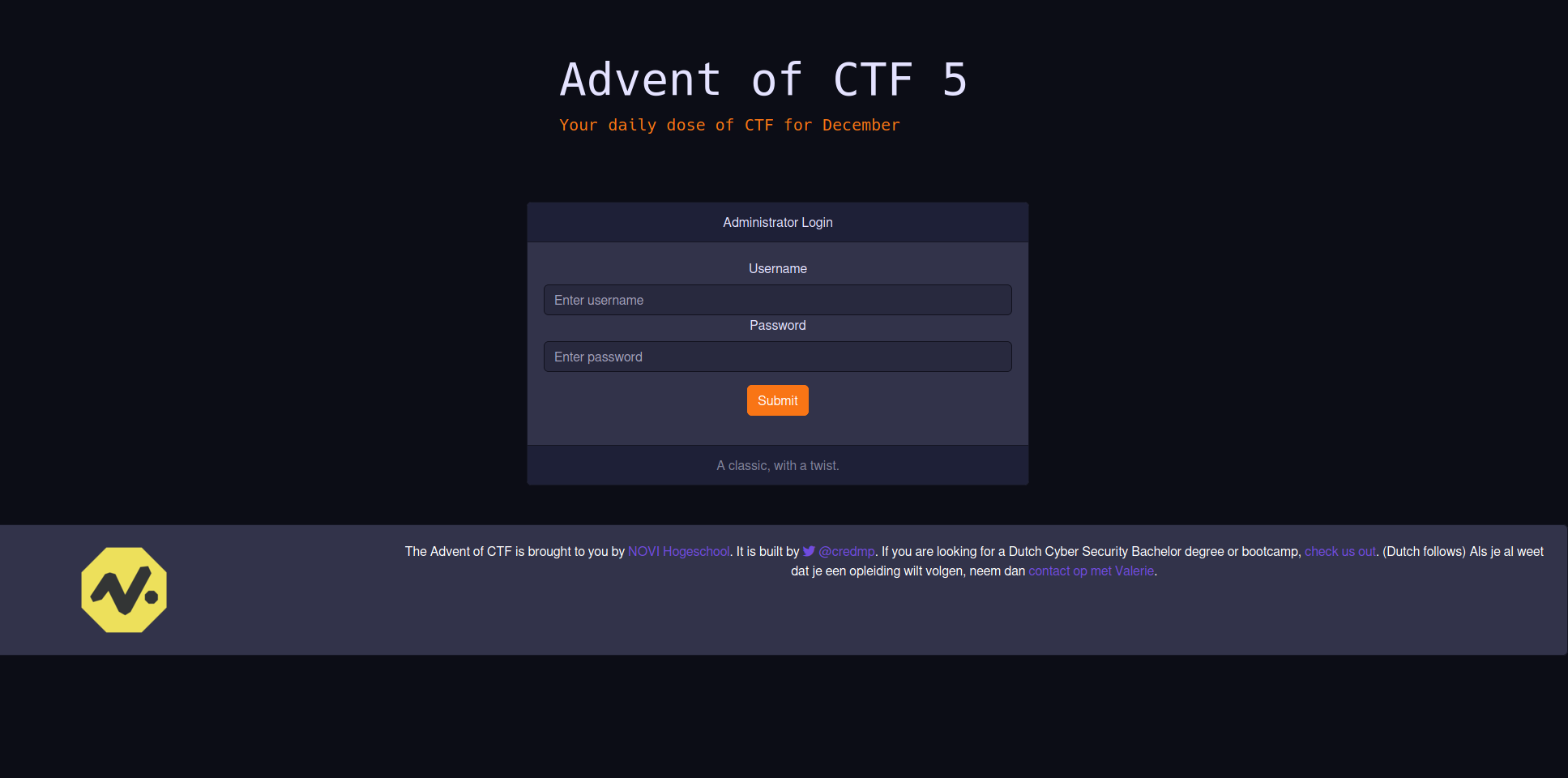
Before we try some more advanced things, let’s first check if the page source holds some hints. Which after looking at it briefly, it doesn’t. In this challenge we’re dealing with a login form. The first thing we should try when we see a login form is a simple SQL injection. For the username and password we try the following values:
username: admin' OR 1=1 password: admin' OR 1=1
Submitting the form with the above as our payload returns the following message:
Error description: You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '' AND password='admin' OR 1=1'' at line 1
While we don’t have the flag yet, this does show that the form is vulnerable to SQL injections. Let’s go a bit further with our injection.
By looking at the error we can make an assumption on how the underlying MySQL query is built (since MariaDB runs upon MySQL).
SELECT * FROM users WHERE username='admin' AND password='obz_is_cool';
What the input we tried above does, is manipulate the query in such a way that it becomes the following:
SELECT * FROM users WHERE usname=' ' OR 1=1 AND password=' ' OR 1=1;
On paper this should work but in this scenario it doesn’t, so we need to find another way. An alternative common SQL flaw is commenting out a part of the query, let’s try that
username: admin' -- password: obz_is_cool
Note: make sure to have a trailing space at the end of --
Submitting this as our form data gives us the flag! NOVI{th3_classics_with_a_7wis7}
On to the next challenge: Advent of CTF – Day 6 Writeup








2 Comments