How to sniff Wi-Fi Probe Requests
Ever wondered what happens when you remember a Wi-Fi station on your phone, laptop or tablet? Always thought this information would only stay on your phone? Guess what, this is not true! The information is freely available for everyone within a short range of your device. All devices containing a Wi-Fi transmitter are constantly sending so-called Wi-Fi probe requests in the open. This requests will not only transmit some of the access points you were connected to, but also reveal nearby access points in the area. This type of requests are sent so that devices are able to identify nearby access points faster.
Wi-Fi probe requests can easily be detected by a tool called ProbeQuest. ProbeQuest depends on Netaddr and Libdnet. These need to be installed prior to the installation of ProbeQuest.
Installation
Installation is pretty straightforward. If you you use Pip you only have to run one command.
sudo pip3 install --upgrade probequest
You can also install probequest by installing from its sources.
git clone https://github.com/SkypLabs/probequest.git cd probequest sudo pip3 install --upgrade .
Please note that pip3 is a Python3 installation tool. You need to have Python3 installed in order to run this command.
Usage
Now that you have ProbeQuest installed you have to put your wireless card into monitor mode. This can be done by creating a virtual antenna or by putthing the current antenna in manual mode.
Code for putthing the antenna in monitor mode
sudo ifconfig <wireless interface> down sudo iwconfig <wireless interface> mode monitor sudo ifconfig <wireless interface> up
Code for creating a virtual antenna
sudo airmon-ng check kill sudo airmon-ng start <wireless interface>
In both cases the <wireless interace> can be found by using ifconfig. The output displays all the interfaces. Normally the name of the wireless interface is something like wlan0, but it can also be wlp3s0.
Run probequest by using the following command:
sudo probequest -i wlan0
Now you can monitor the outgoing requests by the router and the requests by the searching devices. You are able to see MAC addresses of the sending devices and the SSID send and received by the devices.
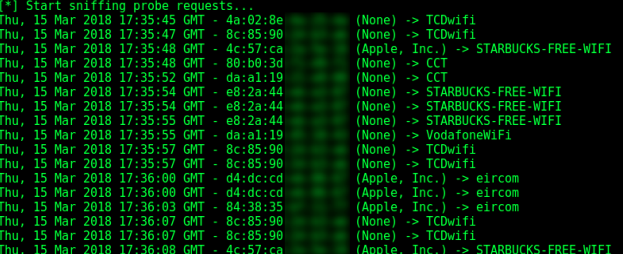
Risks
By monitoring a device for some time within the network, an attacker would be able to pinpoint where and how long someone stays within the same place. The hardware address is sent within the probe request as well. This will help attackers in profiling its victims. This technique can be used by a boss of a company to monitor how long its employees are taking a break. More likable examples are: providing personalized advertisements or analyzing visitor flows at airports.
Besides profiling an attackers is also able to perform another type of attack. Devices are also sending their known Access points. This means that Wi-Fi probe requests can be abused to connect a victim’s device to a fake network. For instance a device sends out a probe request containing the SSID: “StarBucks Free-WiFi”. Normally this access point does not require a password. Now an attacker can provide a fake network with the same SSID to lure a victim into changing its Wi-Fi connection. Once the device of the victim changed its Wi-Fi connection, an attacker would be able to sniff all the data received and sent by the victim over Wi-Fi.
Solutions
Your device can be sending Wi-Fi probe requests all the time. Most devices can be configured to only send Wi-Fi probe requests when necessary. This option can be found in the Settings app for Android. iOS devices already are configured to only send probe requests when necessary. Furthermore, it would be smart to forget most of your connected access points. This would prevent an attacker to hijack your Wi-Fi connection.








